AWS Config Rule: Kinesis Encryption
CHECK_FOR_ENCRYPTION_KINESIS
Ryan Ware
Last Update hace 10 meses
Description: Checks whether Kinesis have Encryption Enabled
Trigger type: Periodic
AWS Region: All supported AWS regions
How to Resolve Manually
By Default, most Amazon Kinesis Data Streams are created without encryption as default. In order to ensure your Amazon Kinesis Encryption Config Rule is returning COMPLIANT, you will need to encrypt your Data Stream with either a customer managed key (CMK) stored within your own KMS vault, or use the default AWS managed CMK (aws/kinesis)
To enable this, you will need to head on over to your Amazon Kinesis dashboard within your AWS Console, view your Data Streams and choose your Stream you would like to encrypt. Within the Configuration tab, look for encryption and choose Edit Encryption to enable and configure this to your liking.
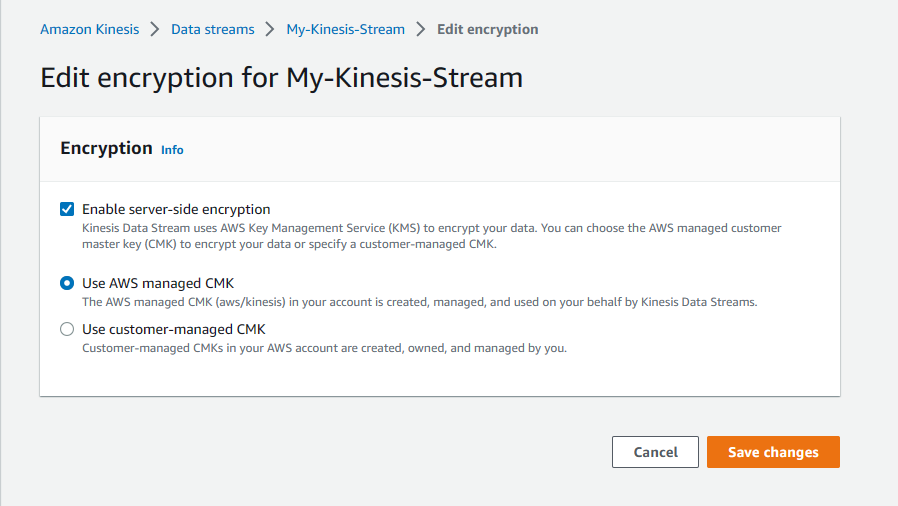
Server-side encryption in Amazon Kinesis Data Streams automatically encrypts data before it's at rest by using an AWS KMS customer master key (CMK) that you specify. Data is encrypted before it's written to the Kinesis stream storage layer. It's decrypted after it’s retrieved from storage. As a result, your data is encrypted at rest within the Kinesis Data Streams service.
How to Resolve with StackZone
StackZone will be able to automatically enable encryption on your Amazon Kinesis Data Streams if you enable this remediation. The remediation action will use the AWS managed CMK (aws/kinesis) when performing the encryption of your Amazon Kinesis Data Streams
This will then ensure that your resources are marked as COMPLIANT with the AWS Config Rule.
To enable this within your own StackZone deployment, head on over to Baseline Services > AWS Config Rules Regional > Kinesis Encryption and enable the remediation.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


