AWS Config Rule: Check For SQS Encrypted
SQS_ENCRYPTED
Ryan Ware
Last Update 2 năm trước
Description: Checks if your Amazon Simple Queue Service (SQS) has encryption enabled
Trigger type: Configuration changes
AWS Region: All supported AWS regions
How to Resolve Manually
To resolve this manually, you will need to encrypt each NON_COMPLIANT SQS Queue with either a key from your KMS Store, or Amazon SQS Key (SSE-SQS) which Amazon creates, manages and uses for you.
Navigate to your SQS Dashboard within your AWS Console. Choose an SQS Queue from the list of Queue's you'd like to enable encryption on, from the tabs at the bottom, choose Encryption.
Here you will receive a small summary regarding your encryption if enabled, such as the CMK alias in use.
To enable encryption on your Amazon SQS Queue, select Edit on this tab and look for Encryption, as pictured below.
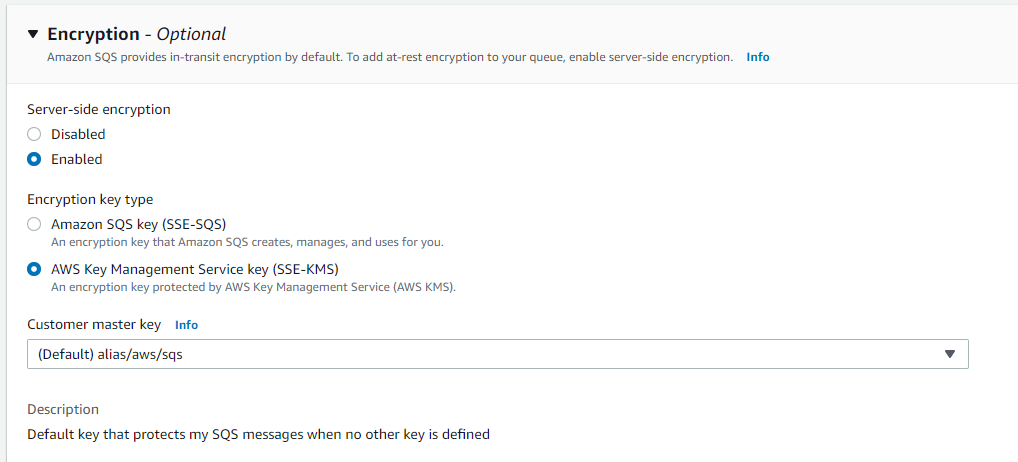
Select your desired Encryption key type and appropriate key alias if applicable. Once you are happy with these settings, click save to encrypt your SQS Queue!
How to Resolve with StackZone
The remediation action which StackZone can perform as part of this AWS Config Rule will allow StackZone to automatically encrypt all of your NON_COMPLIANT Amazon SQS Queue's with the default AWS SQS CMK.
This is the default AWS Customer Managed Key for SQS and is cheaper to use than a custom key uploaded to your key store for SQS.
To enable this for your StackZone deployment, head on over to Provisioning / Baseline Services / Config Rules Regional / Amazon SQS and enable the remediation.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


