AWS Config Rule: GuardDuty Non Archived Findings
GUARDDUTY_NON_ARCHIVED_FINDINGS
Fernando Honig
Last Update één jaar geleden
Description: Checks whether Amazon GuardDuty has findings that are non archived. The rule is NON_COMPLIANT if Amazon GuardDuty has non archived low/medium/high severity findings older than the specified number in the daysLowSev/daysMediumSev/daysHighSev parameter.
Trigger type: Periodic
AWS Region: All supported AWS regions except Israel (Tel Aviv), Canada West (Calgary) Region
How to Resolve Manually
GuardDuty has default days per severity in which findings are allowed to stay non-archived;
- Low Severity: 30 Days
- Medium Severity: 7 Days
- High Severity: 1 Day
These values can be changed within your config rule if you require different values.
If you see the example below, we have a Low Severity example which was last seen 8 days ago. This falls within the default acceptable range for a Low Severity finding. If this were to exceed 30 days and had not yet been archived, it would trigger this config rule and become NON_COMPLIANT.
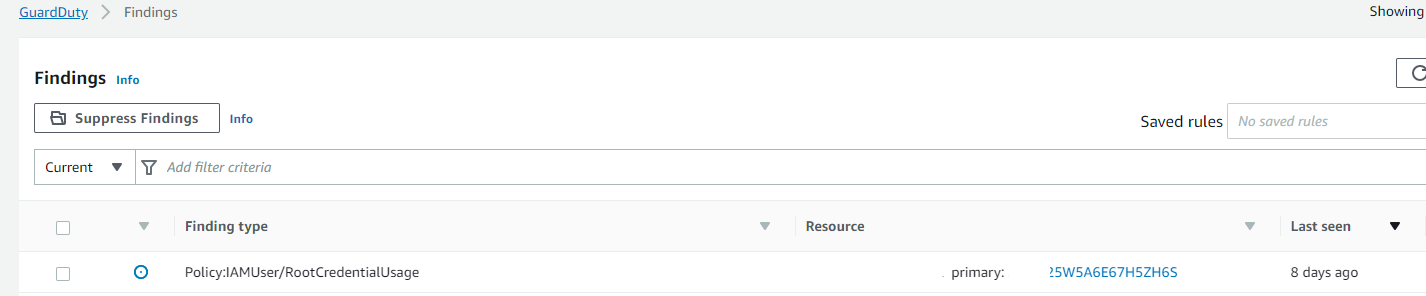
You can use Suppress Findings to group findings based on criteria, and the suppression rules option will allow you to automatically archive findings matching these criteria's. You can use these supression rules to hide recurrent findings that you do not intend to act on.
However, this doesn't mean that all GuardDuty findings should be ignored - if you can resolve the findings instead of supressing them, then you should! For example the finding above can be easily resolved by ensuring the root account is not used, and that this person uses an IAM user or Role instead.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


