AWS Config Rules: IAM Inline Policy Blocked KMS Actions
IAM_INLINE_POLICY_BLOCKED_KMS_ACTIONS
Eduardo Van Cauteren
Last Update 9 maanden geleden
Description: Checks if the inline policies attached to your IAM users, roles, and groups do not allow blocked actions on all AWS KMS keys. The rule is NON_COMPLIANT if any blocked action is allowed on all AWS KMS keys in an inline policy.
Trigger type: Configuration changes
AWS Region: All supported AWS regions
How to Resolve Manually
This Config Rule checks that the inline policies attached to IAM Users, Roles or Groups doesn't include any of the blocked KMS actions patterns defined within the StackZone's Console. The rule will be marked as non-compliant if a policy is found granting permissions using one of the blocked actions.
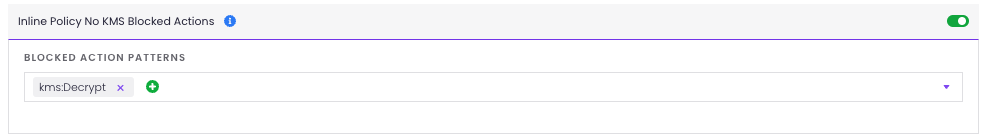
For this rule to work, you need to first define the Blocked Action Patterns, this mean to define a list of forbidden actions for the rule to check. For example: kms:*, kms:Decrypt, kms:ReEncrypt*
To do so, login into StackZone console and go to Provisioning > Baseline Resources > Config Rules Global and click on IAM. Locate the Inline Policy No KMS Blocked Actions card. Toggle on Edit mode and the rule's card as well.
Fill in the Blocked Action Patterns field with the desired actions to be checked and click on Save Settings button. Finally go to Provisioning > Status and deploy the changes to your AWS environment. Check the following screenshot for reference:
In order to resolve a non-compliant resource, you will need to edit or remove the inline policy to not include any of the blocked action patterns you defined.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


