AWS Config Rules: IAM Policy in Use
IAM_POLICY_IN_USE
Eduardo Van Cauteren
Last Update il y a 9 mois
Description: Checks whether the IAM policy ARN is attached to an IAM user, or a group with one or more IAM users, or an IAM role with one or more trusted entity. Note: about Managed Rules and Global IAM Resource Types, please read here.
Trigger type: Periodic
AWS Region: All supported AWS regions
How to Resolve Manually
This Config Rule checks if a certain IAM policy is attached to a User, Group or Role. The rule will be marked as non-compliant if the IAM Policy is unattached to any of the mentioned resources.
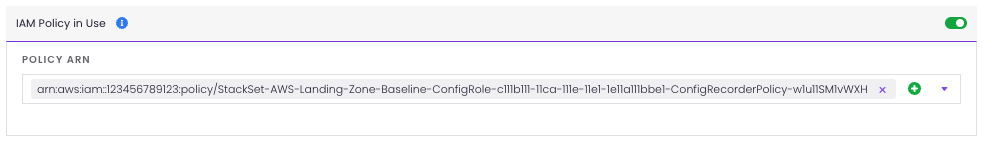
For this Rule to work, you first need to specify the Policy ARN to be checked. To do this, login into StackZone console and go to Provisioning > Baseline Services > Config Rules Global and then go to IAM. From there look for the IAM Policy in Use card and fill in the Policy ARN field with the desired value. Click on Save Settings then go to Provisioning > Status to finally click on the Deploy button. Use the following picture as a visual reference:
In the case of the rule detecting a non-compliant resource, you will need to attach the IAM Policy to a user, group or role, or remove it if it's not actually needed.
Notice that this Config Rule checks only one ARN at a time.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


