AWS Config Rule: SageMaker Notebook Instance KMS Key Configured
SAGEMAKER_NOTEBOOK_INSTANCE_KMS_KEY_CONFIGURED
Fernando Honig
Last Update 10 miesięcy temu
Description: Check whether an AWS Key Management Service (KMS) key is configured for an Amazon SageMaker notebook instance. The rule is NON_COMPLIANT if 'KmsKeyId' is not specified for the Amazon SageMaker notebook instance.
Trigger type: Periodic
AWS Region: All supported AWS regions except Asia Pacific (Jakarta), Middle East (UAE), Asia Pacific (Hyderabad), Asia Pacific (Melbourne), AWS GovCloud (US-East), AWS GovCloud (US-West), Israel (Tel Aviv), Europe (Spain), Europe (Zurich) Region
How to Resolve Manually
To resolve this manually, head to your AWS SageMaker Dashboard within the AWS Console and take a look at the left hand side menu, you'll want to navigate to Notebook / Notebook Instances.
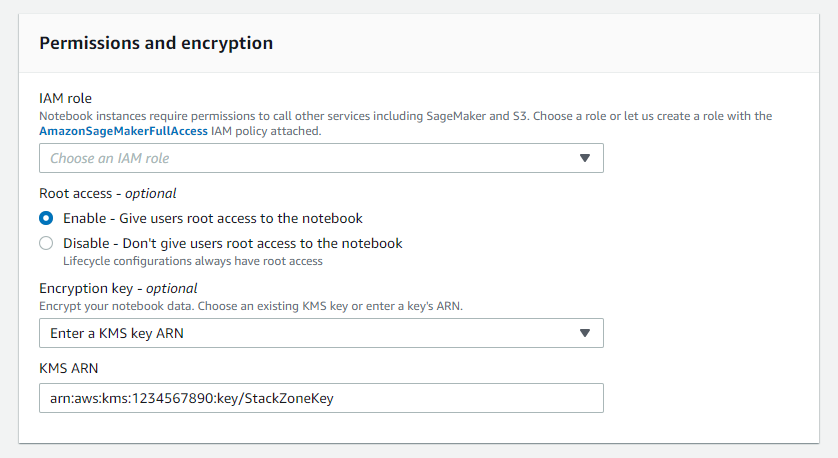
When configuring or modifying a notebook instance, if you take a look at the settings within the Permissions and Encryption section. Here you are able to assign an IAM Role to the Notebook Instance, but more importantly to the above Config Rule, you will be able to encrypt your Notebook data with an AWS KMS Key.
You have the ability to either enter an AWS KMS arn, or choose an existing stored key from your KMS. Either of these options will change this rule to become COMPLIANT.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


