AWS Config Rule: CloudTrail Security Trail Enabled
CLOUDTRAIL_SECURITY_TRAIL_ENABLED
Ryan Ware
Last Update год назад
Description: Checks that there is at least one AWS CloudTrail trail defined with security best practices. This rule is COMPLIANT if there is at least one trail that meets all of the following:
- records global service events
- is a multi-region trail
- has Log file validation enabled
- encrypted with a KMS key
- records events for reads and writes
- records management events
- does not exclude any management events
This rule is NON_COMPLIANT if no trails meet all of the criteria mentioned above.
Trigger type: Periodic
AWS Region: All supported AWS regions
How to Resolve Manually
There are a number of items to resolve, as listed above, in order to ensure that your CloudTrail Trail is COMPLIANT with this particular AWS Config Rule. Some of these are quite basic and can be enabled through the CloudTrail dashboard by clicking "Edit" within your Trail.
Basic Resolutions:
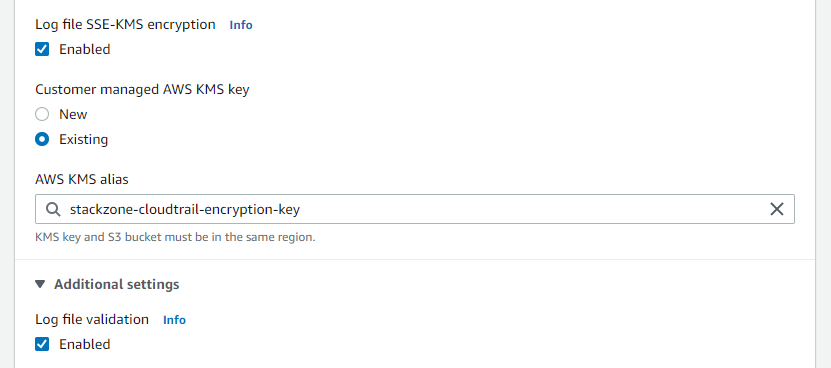
- Log File encrypted with a KMS Key
- Log File validation enabled
These two items can be enabled very easily by editing your current Trail. To do this, head on over to your CloudTrail Dashboard within your AWS Console and click "Edit" to view and change these settings
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


