AWS Config Rule: CodeBuild Plaintext Creds. in Env. Variables
CODEBUILD_PROJECT_ENVVAR_AWSCRED_CHECK
Fernando Honig
Last Update setahun yang lalu
Description: Checks whether the project contains environment variables AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY. The rule is NON_COMPLIANT when the project environment variables contains plaintext credentials.
Trigger type: Configuration changes
AWS Region: All supported AWS regions except Asia Pacific (Jakarta), Asia Pacific (Hyderabad), Israel (Tel Aviv), Canada West (Calgary), Europe (Spain), Europe (Zurich) Region
How to Resolve Manually
To resolve this manually, sign in to your AWS Management Console and select CodeBuild under Services.
Click on the Code Build Project that is NON_COMPLIANT and then click on Edit.
Check the Environment variables and make sure to replace the AWS_ACCESS_KEY and AWS_SECRET_ACCESS_KEY as Plaintext by a Parameter or Secrets Manager
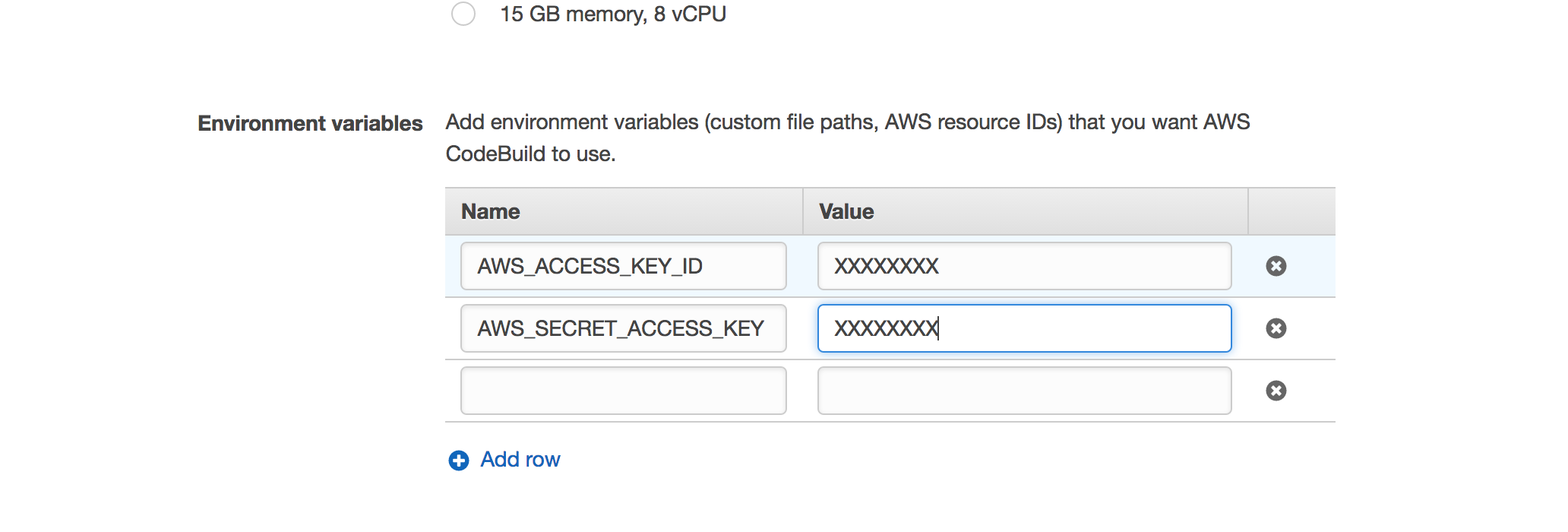

How to Resolve with StackZone
In order to resolve this trough automation, login into StackZone Console, locate Provisioning at the left side menu and go to Baseline Services -> Config Rules Regional -> Development, then look for Remediation(s) card and enable the CodeBuild Plaintext Credentials in Environment Variables Remediation.
Once the previous step is completed, click on Save Settings button then go to Provisioning -> Status and click on the Deploy button. Notice that the deployment process will take some time to finish from the AWS side.
This remediation will delete the AWS_ACCESS_KEY and AWS_SECRET_ACCESS_KEY environment variables, from any CodeBuild project, if they contain plaintext credentials.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


