AWS Config Rule: EC2 Instance Profile Attached
EC2_INSTANCE_PROFILE_ATTACHED
Ryan Ware
Last Update vor einem Jahr
Description: Checks if an Amazon Elastic Compute Cloud (Amazon EC2) instance has an Identity and Access Management (IAM) profile attached to it. This rule is NON_COMPLIANT if no IAM profile is attached to the Amazon EC2 instance.
Trigger type: Configuration changes
AWS Region: All supported AWS regions except China (Beijing), Asia Pacific (Jakarta), Asia Pacific (Hyderabad), Asia Pacific (Osaka), Canada West (Calgary), Europe (Spain), China (Ningxia) Region
How to Resolve Manually
To resolve this manually, you will need to first head on over to your Amazon EC2 Dashboard within the AWS Console.
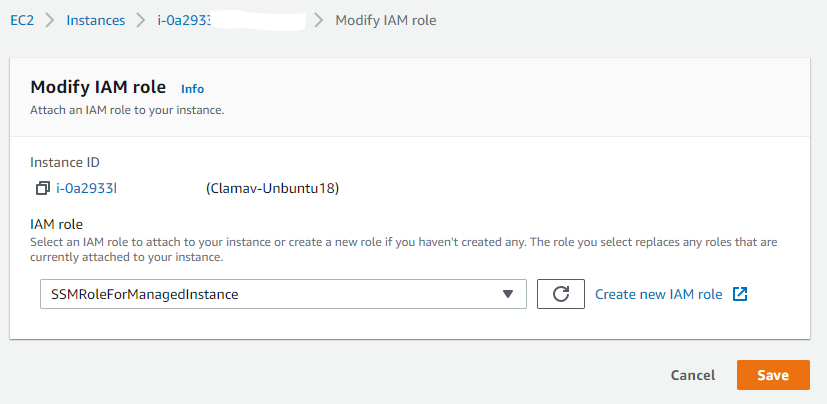
Select your EC2 Instance that you wish to assign an IAM Role to, and from the Actions Menu, select Security and then Modify IAM Role.
Once you have clicked this, you will be met with this options menu pictured below. You are able to select from a drop-down list of IAM Role which are available to be attached to an EC2 Instance as an Instance Profile. If none are applicable, AWS will allow you to create an IAM Role using the link provided, which will open a second window.
Once you have an appropriate IAM Role selected, press Save to attach this IAM Role to your Amazon EC2 Instance, this will then mark the EC2 Instance as COMPLAINT with regards to this AWS Config Rule.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


