AWS Config Rule: ELBV2 ACM Certificate Required
ELBV2_ACM_CERTIFICATE_REQUIRED
Ryan Ware
Last Update één jaar geleden
Description: Checks if Application Load Balancers and Network Load Balancers have listeners that are configured to use certificates from AWS Certificate Manager (ACM). This rule is NON_COMPLIANT if at least 1 load balancer has at least 1 listener that is configured without a certificate from ACM or is configured with a certificate different from an ACM certificate.
Trigger type: Periodic
AWS Region: All supported AWS regions except Asia Pacific (Jakarta), Middle East (UAE), Asia Pacific (Hyderabad), Asia Pacific (Osaka), Asia Pacific (Melbourne), AWS GovCloud (US-East), AWS GovCloud (US-West), Israel (Tel Aviv), Canada West (Calgary), Europe (Spain), Europe (Zurich) Region
How to Resolve Manually
This AWS Config Rule will check if your Application Load Balancer (ALB) or Network Load Balancer (NLB) have SSL listeners that are configured to use certificates from AWS Certificate Manager (ACM)
To resolve this manually, you will need to ensure that you are using a certificate from AWS Certificate Manager (ACM) to certify an SSL or HTTPS listener which exists on your Load Balancer in question. Whilst you do have the option to upload a certificate to IAM and choose one from there, it is recommended to use one from ACM as you can offload the certificate renewal to ACM.
When constructing Listeners for your ALB or NLB, you have the option to configure the above in any HTTPS Listener. We add the Certificate from ACM as the Default SSL cert to the particular Load Balancer Listener.
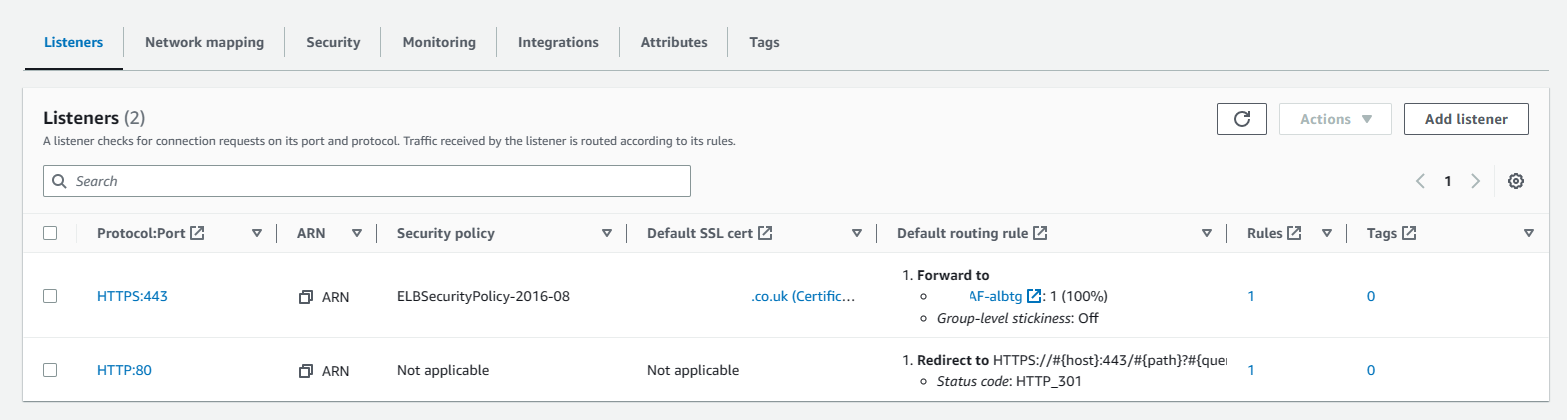
Please see above for an example on how to choose the correct configuration, providing you have a certificate ready to go.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


