AWS Config Rule: NACL No Unrestricted SSH RDP
NACL_NO_UNRESTRICTED_SSH_RDP
Eduardo Van Cauteren
Last Update un anno fa
Description: Checks if default ports for SSH/RDP ingress traffic for network access control lists (NACLs) is unrestricted. The rule is NON_COMPLIANT if a NACL inbound entry allows a source TCP or UDP CIDR block for ports 22 or 3389.
Trigger type: Configuration changes
AWS Region: All supported AWS regions
How to Resolve Manually
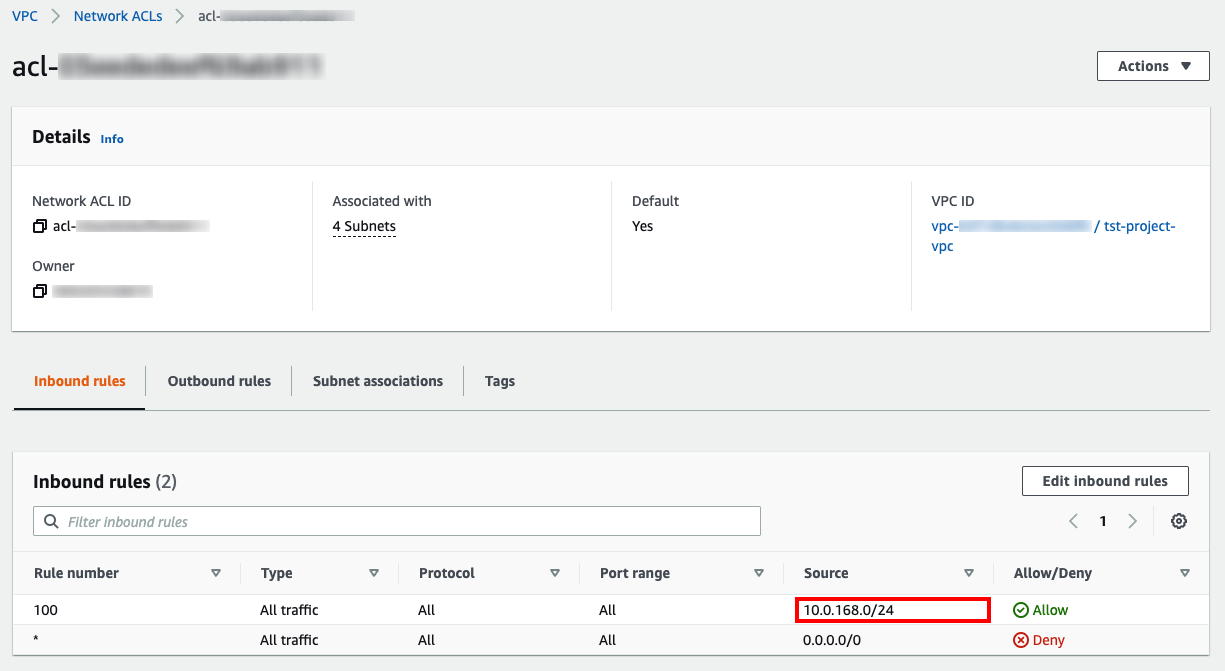
This rule checks whether you have unrestricted TCP or UDP ingress traffic for SSH or RDP ports (22 and 3389 respectively) in any of your network access control lists (NACLs). Note that if you have any inbound rule that allows ingress traffic for all ports from all sources, the config rule will be also marked as non-compliant.
To resolve this manually, ensure that all of your inbound rules within your NACLs only allow ingress traffic for ports 22 or 3389 (or a range containing these ports) from a specific subnet or IP address. Check the following screenshot as a reference:
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


