AWS Config Rule: RDS Cluster Default Admin Check
RDS_CLUSTER_DEFAULT_ADMIN_CHECK
Eduardo Van Cauteren
Last Update a year ago
Description: Checks if an Amazon Relational Database Service (Amazon RDS) database cluster has changed the admin username from its default value. The rule is NON_COMPLIANT if the admin username is set to the default value.
Trigger type: Configuration changes
AWS Region: All supported AWS regions except Middle East (Bahrain), China (Beijing), Asia Pacific (Jakarta), Middle East (UAE), South America (Sao Paulo), Asia Pacific (Hyderabad), Asia Pacific (Melbourne), AWS GovCloud (US-East), AWS GovCloud (US-West), Israel (Tel Aviv), Europe (Spain), China (Ningxia), Europe (Zurich) Region
How to Resolve Manually
A general security recommendation is not to use the default admin usernames for resources. This rule checks that 'postgres' or 'admin' usernames are not being used for any of the RDS Clusters. If one of those usernames are found in any of the RDS Clusters the rule will be marked as non-compliant.
To check the current master username of a cluster, head to AWS Console, go to RDS and click on DB Clusters from within the Dashboard. Check that any of the listed DB Clusters have the master username different than 'postgres' or 'admin' in order to make the resource compliant. Check the following screenshot as a reference:
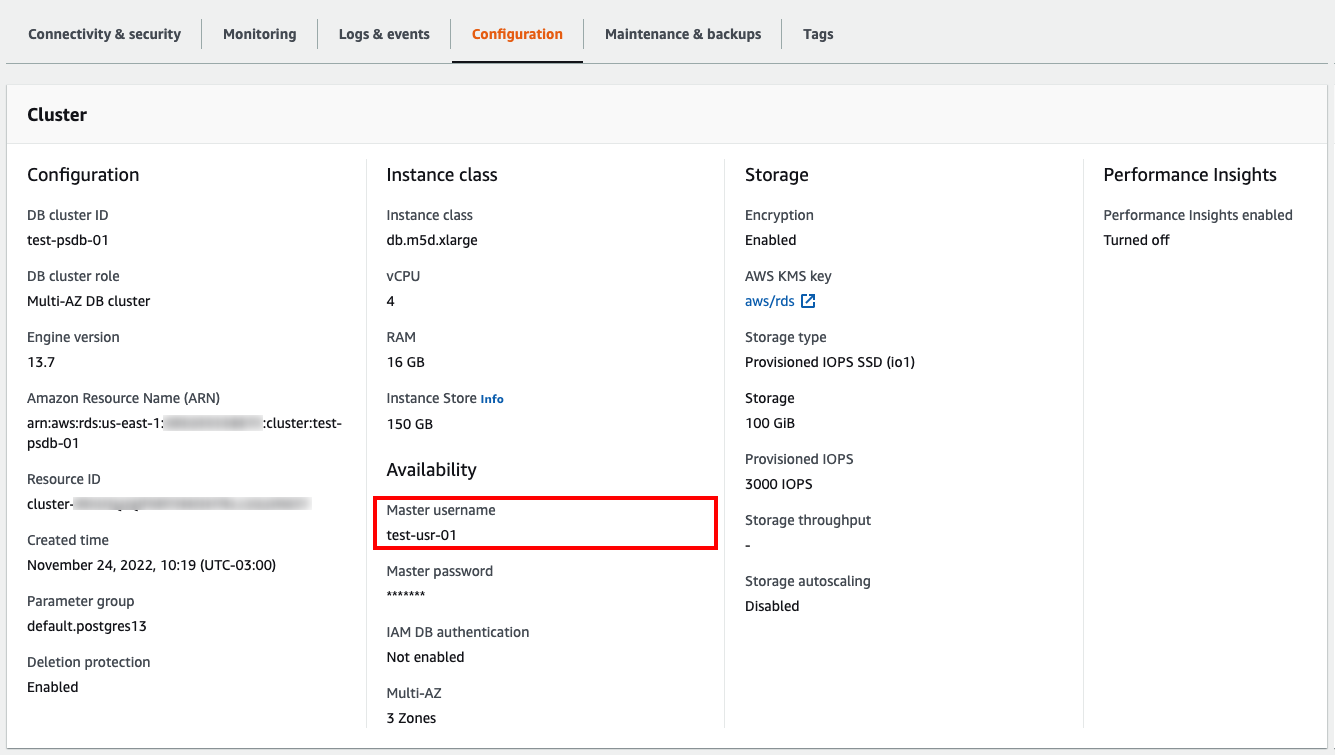
AWS indicates in the documentation that you can't change the master user name after the DB Cluster is created, so you will have to develop an appropriate process that fits the needs of your current infrastructure.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


