AWS Config Rule: RDS Cluster IAM Authentication Enabled
RDS_CLUSTER_IAM_AUTHENTICATION_ENABLED
Eduardo Van Cauteren
Last Update a year ago
Description: Checks if an Amazon RDS Cluster has AWS Identity and Access Management (IAM) authentication enabled. The rule is NON_COMPLIANT if an RDS Cluster does not have IAM authentication enabled.
Trigger type: Configuration changes
AWS Region: All supported AWS regions except Middle East (Bahrain), China (Beijing), South America (Sao Paulo), Asia Pacific (Hyderabad), Asia Pacific (Osaka), Asia Pacific (Melbourne), AWS GovCloud (US-East), AWS GovCloud (US-West), Israel (Tel Aviv), Europe (Spain), China (Ningxia) Region
How to Resolve Manually
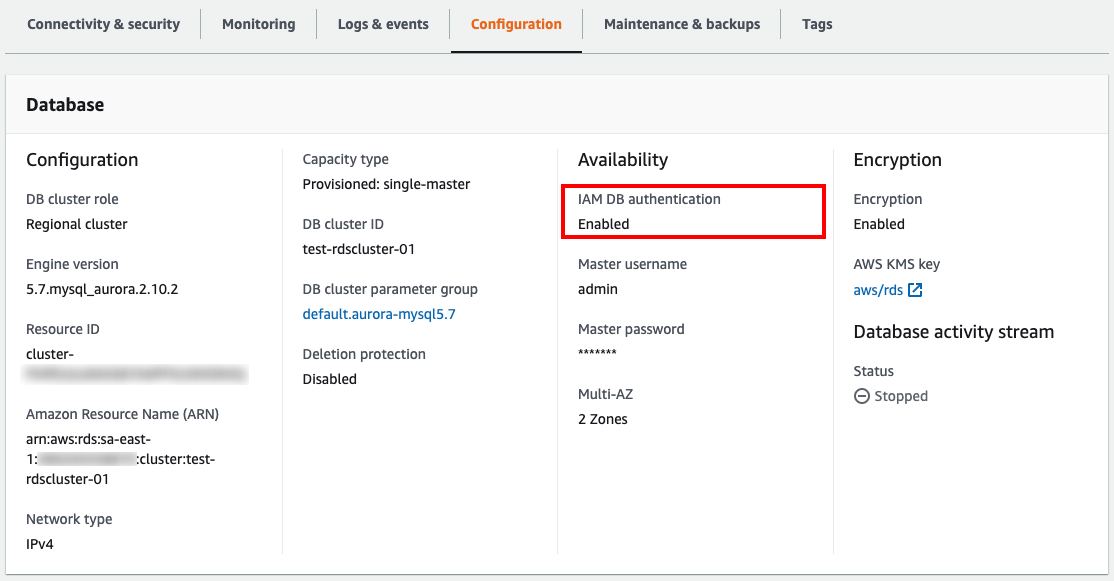
This rules checks whether Identity and Access Management (IAM) authentication is enabled for a specific Amazon RDS database cluster. If the database authentication is configured as password authentication, the rule will be marked as non-compliant. Notice that the IAM Authentication option is only is available for clusters of the RDS Aurora type.
To resolve this, you need to check the current database authentication of an instance. Head to AWS Console, go to RDS service and click on DB Clusters from within the Dashboard. Then click on the name of the desired cluster, go to the Configuration tab to check the current IAM DB authentication status. In case it's Disabled, click on Modify button to open the configuration screen then look for the Database authentication card and choose the Password and IAM database authentication option; click Continue to review the Summary of modifications then finally click on Modify DB Cluster button to apply changes. Check the following screenshot as reference:
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


