AWS Config Rule: RDS Logging Enabled
RDS_LOGGING_ENABLED
Fernando Honig
Last Update hace un año
Description: Checks if log types exported to Amazon CloudWatch for an Amazon Relational Database Service (Amazon RDS) instance are enabled. The rule is NON_COMPLIANT if any such log types are not enabled.
Trigger type: Configuration changes
AWS Region: All supported AWS regions except Africa (Cape Town), Asia Pacific (Hyderabad), Asia Pacific (Osaka), Europe (Milan), Europe (Spain) Region
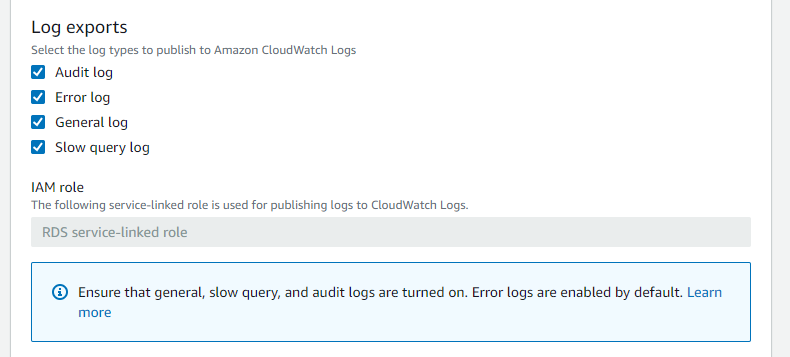
How to Resolve Manually
To resolve this manually, you will need to ensure that logging is enabled when creating an RDS instance and that you select one or more logs to export to CloudWatch. It's good practice to ensure that these four are all turned on by default.
The RDS service-linked role is used to publish your log files to CloudWatch Logs - so there is no additional permissions to worry about for this stage here.
By ensuring these log files are exported to CloudWatch Logs - you will then be COMPLIANT with the above config rule.
How to Resolve with StackZone
Note: This remediation is only compatible with MySQL Engine. (This does not include MySQL-Aurora)
You can optionally remediate any RDS DB Instance so that logging is created for you and sent to CloudWatch Logs
In order to enable this remediation, in the StackZone console navigate to Provisioning / Baseline Services / AWS Config Rules Regional / Amazon RDS and enable RDS Logging Enabled Remediation
Note: this is still an experimental Remediation. In order to use it, you have to enable "Experimental Features" in the StackZone Settings -> Organization Details section.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


