AWS Config Rule: VPC Restricted SSH Policy
INCOMING_SSH_DISABLED
Ryan Ware
Last Update un anno fa
Description: Checks if the incoming SSH traffic for the security groups is accessible. The rule is COMPLIANT when IP addresses of the incoming SSH traffic in the security groups are restricted (CIDR other than 0.0.0.0/0). This rule applies only to IPv4.
Trigger type: Configuration changes
AWS Region: All supported AWS regions except Africa (Cape Town), Europe (Milan) Region
How to Resolve Manually
Incoming SSH Disabled focuses on TCP Port 22 within your EC2 Security Groups.
Similar to the AWS Config Rule Restricted Common Ports Policy, if you are allowing Port 22 to be accessible from anywhere (0.0.0.0/0) this will most certainly be flagged as NON_COMPLIANT as well as being quite a security risk for your server configuration.
Having Port 22 accessible by such a wide scope is poor practice, and considered by many a security risk as it opens the possibility for brute force SSH attacks into your Linux Servers.
If you have an EC2 Security Group created with an ingress rule for Port 22, it must be controlled by limiting the scope to an IP address or CIDR other than 0.0.0.0/0
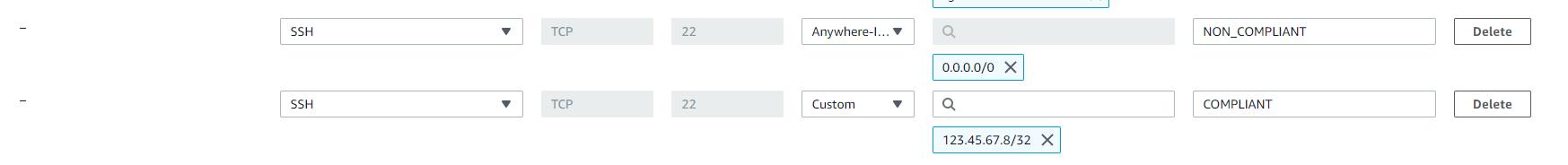
Resolving this will take some time, as you will need to audit all NON_COMPLIANT Security Group resources to find which rules are causing your resources to be NON_COMPLIANT. You will then need to lower the scope of your ingress rules to restrict access.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


