AWS Config Rule: EBS Snapshot Not Public Restorable
EBS_SNAPSHOT_PUBLIC_RESTORABLE_CHECK
Fernando Honig
Last Update setahun yang lalu
Description: Checks whether Amazon Elastic Block Store (Amazon EBS) snapshots are not publicly restorable. The rule is NON_COMPLIANT if one or more snapshots with RestorableByUserIds field are set to all, that is, Amazon EBS snapshots are public.
Trigger type: Periodic
AWS Region: All supported AWS regions except Europe (Spain) Region
How to Resolve Manually
To resolve this manually, you will need to review your collection of Snapshots from the AWS EC2 Dashboard. Under the blue "Create Snapshot" filter there is the option to filter shown snapshots between;
- Public Snapshots
- Private Snapshots
- Owned By Me
Your goal is to ensure that you own only Private Snapshots. This is normally governed by the fact that an EBS Volume is encrypted with a KMS Key. Below is an output of what a Public list of Snapshots look like, and you will first notice that they are all unencrypted.
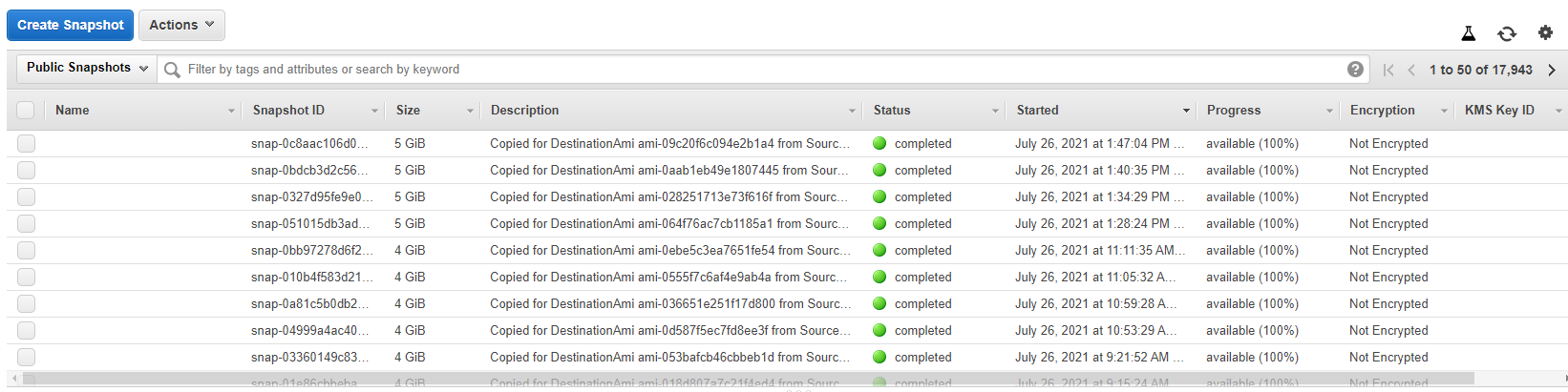
You can make public an EBS Snapshot if you please, but it cannot be done if the Volume is encrypted using the default CMK key. AWS will block you from changing the permissions.
If you ensure that your Volumes are encrypted using an AWS CMK key, you will more than likely ensure they are kept private this way.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


