AWS Config Rule: EC2 No Amazon Key Pair
EC2_NO_AMAZON_KEY_PAIR
Ryan Ware
Last Update één jaar geleden
Description: Checks if running Amazon Elastic Compute Cloud (EC2) instances are launched using amazon key pairs. The rule is NON_COMPLIANT if a running EC2 instance is launched with a key pair.
Trigger type: Configuration changes
AWS Region: All supported AWS regions except China (Beijing), Asia Pacific (Jakarta), Middle East (UAE), Asia Pacific (Hyderabad), Asia Pacific (Melbourne), AWS GovCloud (US-East), AWS GovCloud (US-West), Israel (Tel Aviv), Europe (Spain), China (Ningxia), Europe (Zurich) Region
How to Resolve Manually
It is quite common to launch an Amazon EC2 Instance with a Key Pair - so this AWS Config Rule may seem counter-intuitive at first.
A Key Pair allows a user to remotely connect to the Amazon EC2 Instance, whether it's over SSH or RDP, confident that they have the correct key pair / decrypted password locally. As a Key Pair cannot be changed for a historic EC2 Instance which may have been running for some time, this in some views can be considered a security concern.
Below is part of the configuration when launching a new Amazon EC2 Instance, you would normally assign an existing Key Pair here to your Amazon EC2 Instance or create a new key pair. Instead we are choosing the option to Proceed without a key pair.
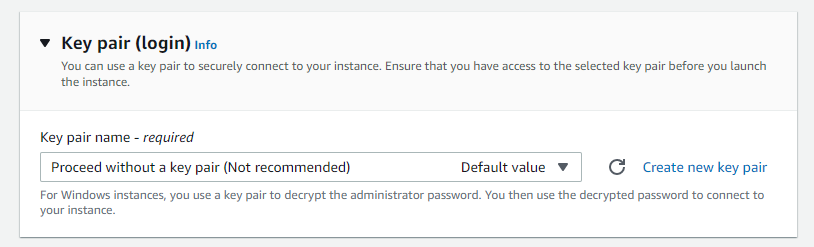
Whilst AWS do not recommend this approach for Amazon EC2 Instances, for this particular AWS Config Rule, AWS is recommending that you do create an Amazon EC2 Instance without a Key Pair - managing access and Instance Management by AWS SSM.
You can still connect to your Amazon EC2 Instance through SSM - almost the same way as you would through RDP / SSH but without the networking overhead. For more on how to do this, check out this article.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


