AWS Config Rule: EKS Endpoint No Public Access
EKS_ENDPOINT_NO_PUBLIC_ACCESS
Luna Ricci
Last Update setahun yang lalu
Description: Checks whether Amazon Elastic Kubernetes Service (Amazon EKS) endpoint is not publicly accessible. The rule is NON_COMPLIANT if the endpoint is publicly accessible.
Trigger type: Periodic
AWS Region: All supported AWS regions except Canada West (Calgary) Region
How to Resolve Manually
You can limit, or completely disable, public access from the internet to your Kubernetes cluster endpoint.
Amazon EKS creates an endpoint for the managed Kubernetes API server that you use to communicate with your cluster (using Kubernetes management tools such as kubectl). By default, this API server endpoint is public to the internet, and access to the API server is secured using a combination of AWS Identity and Access Management (IAM) and native Kubernetes Role Based Access Control (RBAC).
To resolve this manually, you will need to head to your Amazon EKS Dashboard within the AWS Console and take a look at your clusters. Take a look at the networking portion of your currently NON_COMPLAINT EKS Clusters - in particular the Cluster Endpoint Access.
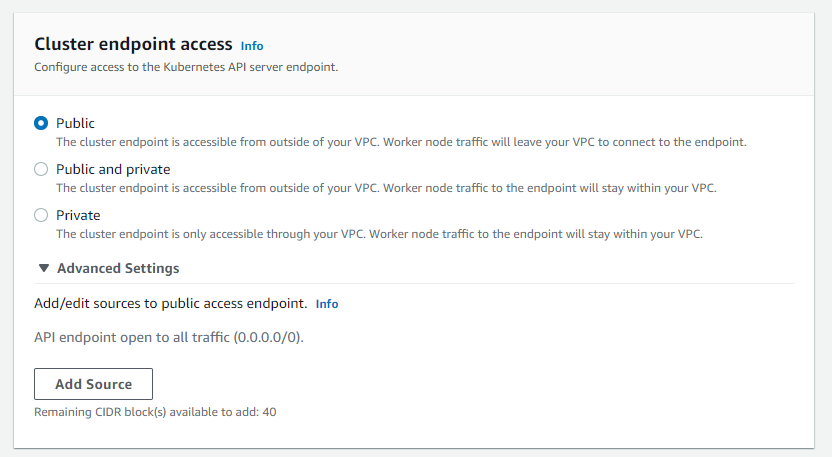
Once you are this particular part of the networking configuration, you will need to switch the Cluster Endpoint Access from Public or Public/Private to Private.
This will then mark your EKS Cluster Endpoint as COMPLIANT in line with the config rule.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


