AWS Config Rule: OpenSearch Node to Node Encryption
OPENSEARCH_NODE_TO_NODE_ENCRYPTION_CHECK
Eduardo Van Cauteren
Last Update 9 months ago
Description: Check if Amazon OpenSearch Service nodes are encrypted end to end. The rule is NON_COMPLIANT if the node-to-node encryption is not enabled on the domain. Note: The rule does not evaluate Elasticsearch domains.
Trigger type: Configuration changes
AWS Region: All supported AWS regions except China (Beijing), Asia Pacific (Jakarta), Africa (Cape Town), Middle East (UAE), Asia Pacific (Hyderabad), Asia Pacific (Osaka), Asia Pacific (Melbourne), Europe (Milan), AWS GovCloud (US-East), AWS GovCloud (US-West), Europe (Spain), China (Ningxia), Europe (Zurich) Region
How to Resolve Manually
This config rule checks if OpenSearch domains have node-to-node encryption enabled. AWS Config will mark the rule as non-compliant if a domain is found with node-to-node encryption disabled.
To resolve this manually, you will need to first head over to the Amazon OpenSearch Service within your AWS Console. Ensure to select the correct region from where your OpenSearch domain is located.
Once there, choose the resource you want to enable the encryption for and then enable Node-to-node encryption from the Security configuration tab. You can use the following screenshot as reference:
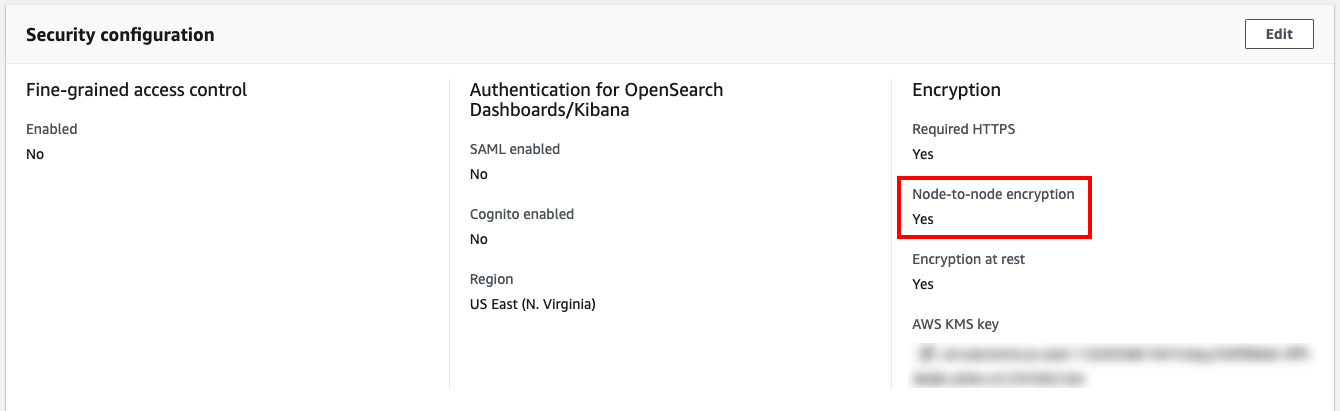
Notice that this rule does not evaluate Elasticsearch domains.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


