AWS Config Rule: RDS Snapshots Public Prohibited
RDS_SNAPSHOTS_PUBLIC_PROHIBITED
Fernando Honig
Last Update год назад
Description: Checks if Amazon Relational Database Service (Amazon RDS) snapshots are public. The rule is NON_COMPLIANT if any existing and new Amazon RDS snapshots are public.
Note: It can take up to 12 hours for compliance results to be captured.
Trigger type: Configuration changes
AWS Region: All supported AWS regions except Africa (Cape Town), Asia Pacific (Melbourne), Europe (Milan), Israel (Tel Aviv), Europe (Spain), Europe (Zurich) Region
How to Resolve Manually
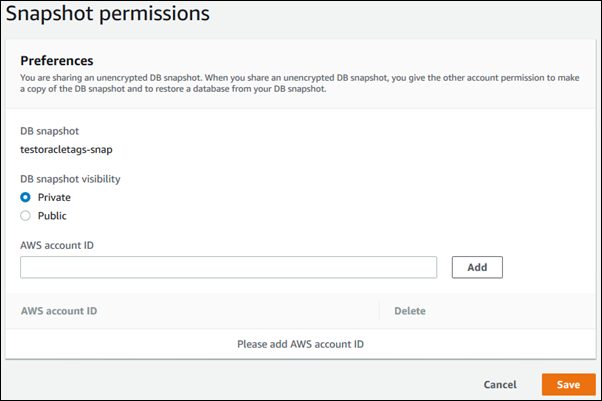
If a Manual DB snapshot visibility is public, all AWS accounts can restore a DB instance from your manual DB snapshot and have access to your data. Do not share any manual DB snapshots that contain private information as Public.
When sharing a snapshot, choose one of the below pictured options for DB snapshot visibility.
- If the source is unencrypted, choose Public to permit all AWS accounts to restore a DB instance from your manual DB snapshot, or choose Private to permit only AWS accounts that you specify to restore a DB instance from your snapshot
- If the source is encrypted, DB snapshot visibility is set as Private because encrypted snapshots can't be shared as Public.
How to Resolve with StackZone
StackZone can automatically resolve your non-compliant RDS DB Instances by running an automation script to change the snapshot visibility to Private.
To enable this remediation, within the StackZone console head on over to Baseline Services -> AWS Config Rules Regional -> PCI-DSS Compliance and enable RDS Snapshot Public Access Prohibited Remediation
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


