AWS Config Rule: Redshift Cluster Configuration Check
REDSHIFT_CLUSTER_CONFIGURATION_CHECK
Ryan Ware
Last Update há um ano
Description: Checks whether Amazon Redshift clusters have the specified settings.
Trigger type: Configuration changes
AWS Region: All supported AWS regions except Middle East (Bahrain), Middle East (UAE), Asia Pacific (Hyderabad), Canada West (Calgary), Europe (Spain) Region
How to Resolve Manually
This AWS Config Rule will check three settings of your Amazon Redshift Clusters in order to register as COMPLIANT.
- Database Encryption must be enabled
- Audit Logging must be enabled
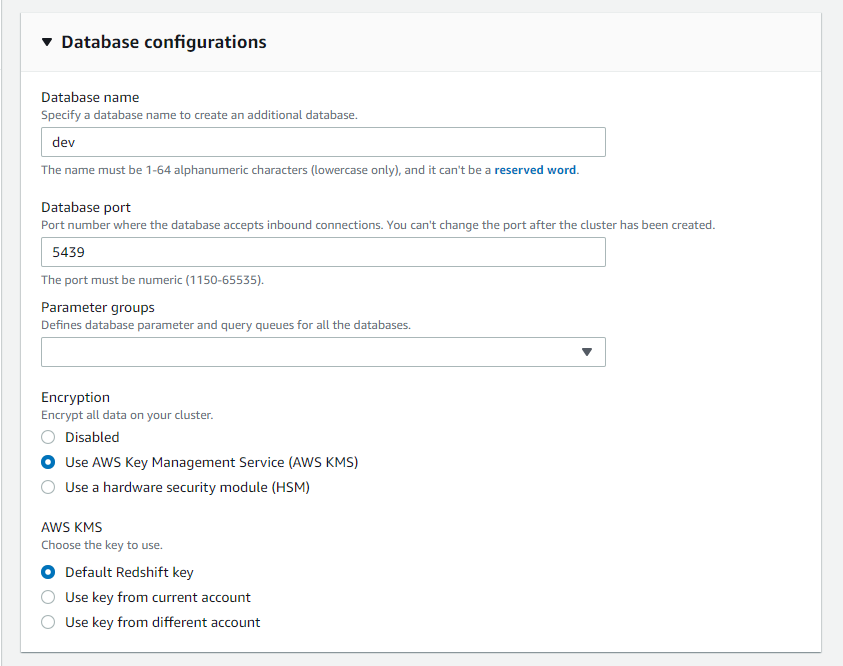
To manually resolve the Redshift Database Encryption, you must first head on over to your Amazon Redshift Dashboard within your AWS Console. From there select your Amazon Redshift Cluster.
Under Additional Configuration / Database Configuration you will see the option to enable encryption and opt to use either the default Redshift AWS KMS Key or your own Customer Managed Key (CMK) within your KMS.
To resolve Audit Logging manually, you will need to enable logging as it is not enabled by default. When you turn on logging on your cluster, Amazon Redshift creates and uploads logs to Amazon S3 that capture data from the time audit logging is enabled to the present time. Each logging update is a continuation of the information that was already logged.
Audit logging to Amazon S3 is an optional, manual process. When you enable logging on your cluster, you are enabling logging to Amazon S3 only. Logging to system tables is not optional and happens automatically for the cluster.
The connection log, user log, and user activity log are enabled together by using the AWS Management Console, the Amazon Redshift API Reference, or the AWS Command Line Interface (AWS CLI). For the user activity log, you must also enable the enable_user_activity_logging database parameter. If you enable only the audit logging feature, but not the associated parameter, the database audit logs log information for only the connection log and user log, but not for the user activity log. The enable_user_activity_logging parameter is not enabled (false) by default. You can set it to true to enable the user activity log. For more information, see Amazon Redshift parameter groups.
How to Resolve with StackZone
With StackZone you can automatically remediate the Redshift Encryption portion of this AWS Config Rule. By enabling this remediation we will run an SSM Document which encrypts your Redshift Cluster with the AWS KMS customer managed CMK.
To enable this in your StackZone deployment, head on over to Provisioning -> BaseLine Services -> Config Rules Regional -> Amazon Redshift and enable Cluster Configuration Check and then enable the Cluster Configuration Check Remediation.
This automation document enables encryption on an Amazon Redshift cluster using the ModifyCluster API. Please note, to encrypt an already encrypted Amazon Redshift cluster using a different KMS key, the cluster's encryption must first be disabled. Also, this document must only be used as a baseline to ensure that your Amazon Redshift clusters are encrypted with the minimum security best practice of using an AWS KMS customer managed CMK. Based on your data policy, clusters should be encrypted with different customer managed CMKs as documented here.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


