AWS Config Rule: S3 Bucket Public Write Prohibited
S3_BUCKET_PUBLIC_WRITE_PROHIBITED
Fernando Honig
Last Update il y a un an
Description: Checks if your Amazon S3 buckets do not allow public write access. The rule checks the Block Public Access settings, the bucket policy, and the bucket access control list (ACL).
Trigger type: Configuration changes
AWS Region: All supported AWS regions
How to Resolve Manually
The rule is compliant when both of the following are true:
- The Block Public Access setting restricts public policies or the bucket policy does not allow public write access.
- The Block Public Access setting restricts public ACLs or the bucket ACL does not allow public write access.
The rule is non-compliant when:
- If the Block Public Access setting does not restrict public policies, AWS Config evaluates whether the policy allows public write access. If the policy allows public write access, the rule is noncompliant.
- If the Block Public Access setting does not restrict public bucket ACLs, AWS Config evaluates whether the bucket ACL allows public write access. If the bucket ACL allows public write access, the rule is noncompliant.
There are 2 ways in which you can resolve this manually. They are both access from the Permissions tab of your S3 Bucket. One way to resolve is to block all public access to your bucket which will outright ensure that your bucket and it's objects are not public.
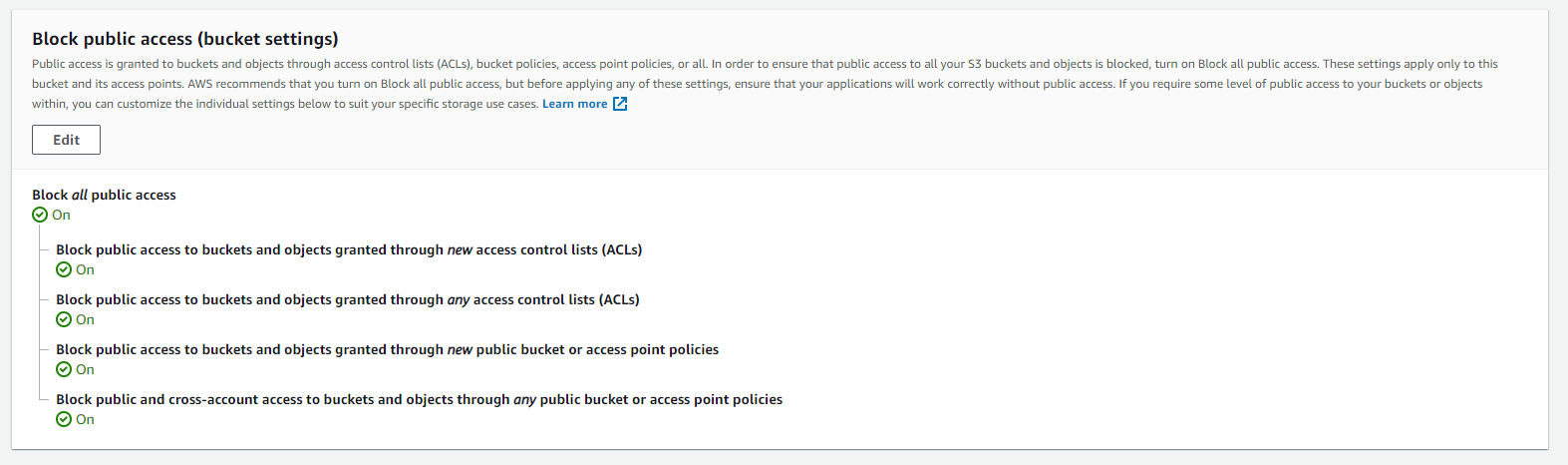
A second way to ensure that public write access is not allowed for your S3 Bucket can be found a little lower within the Permissions tab. These are Access Control Lists (ACLs) and can govern different aspects of who can do what with your objects and bucket overall. Here you can define public read only for example, or public read/write.
The image below shows us that within these ACLs, only our own AWS Account can list, read and write to our bucket.

How to Resolve with StackZone
The Remediation actions which StackZone can perform with this Config Rule will automatically disable S3 Public Write access for any S3 Buckets to be found as NON_COMPLIANT according to this Config Rule
We will call an SSM Document which will be able to make these configurational changes.
To enable this Remediation, head on over to Baseline Services -> Config Rules Regional -> S3 Public Write Prohibited Remediation and enable the remediation for this rule.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


