AWS Config Rule: S3 Default KMS Encryption
S3_DEFAULT_ENCRYPTION_KMS
Luna Ricci
Last Update setahun yang lalu
Description: Checks whether the Amazon S3 buckets are encrypted with AWS Key Management Service(AWS KMS). The rule is NON_COMPLIANT if the Amazon S3 bucket is not encrypted with AWS KMS key.
Trigger type: Configuration changes
AWS Region: All supported AWS regions except Asia Pacific (Hyderabad), Asia Pacific (Osaka), Canada West (Calgary), Europe (Spain) Region
How to Resolve Manually
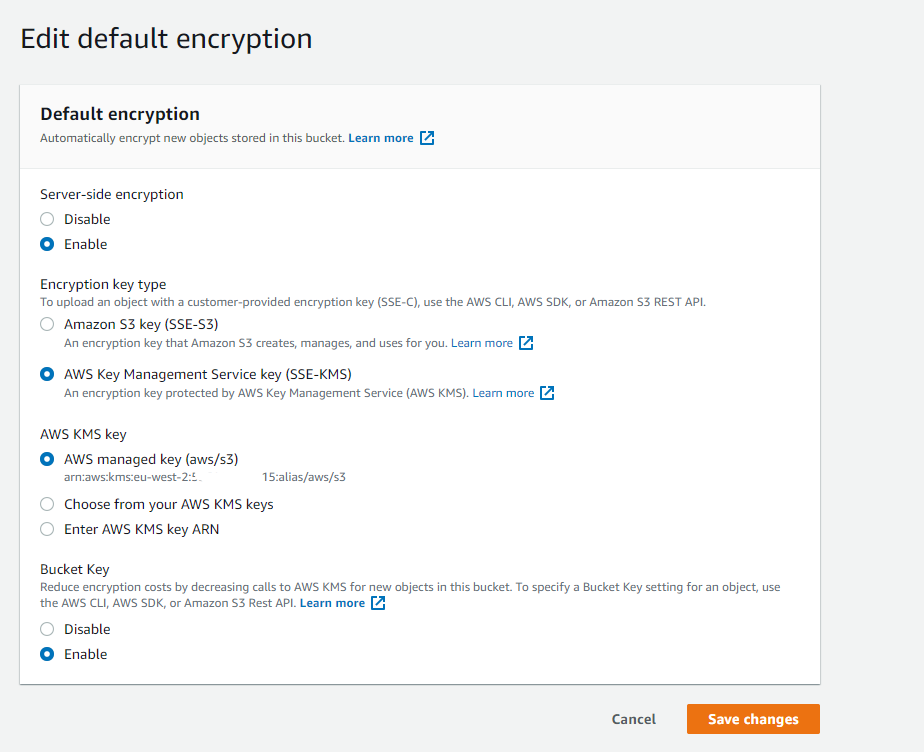
To resolve this manually, you must ensure your S3 Bucket has encryption enabled. Within the S3 Bucket properties tab, head on over to "Default encryption" from here you can select your AWS KMS key and enable default encryption.
How to Resolve With StackZone
StackZone can automatically remediate this for you with the help of KMS and an automated SSM Document.
This Remediation will create for you an S3 KMS CMK in your KMS store for the AWS Account which has the NON_COMPLIANT S3 resource in and it will encrypt the same S3 Bucket with your new S3 CMK
To enable this, head to Provisioning -> Baseline Services -> AWS Config Rules Regional -> Amazon S3 and find the remediation called S3 Bucket KMS Encryption Remediation
You will also be able to define the Key Alias in this step too.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


