AWS Config Rule: Secrets Manager Encrypted Using CMK
SECRETSMANAGER_USING_CMK
Fernando Honig
Last Update год назад
Description: Checks if all secrets in AWS Secrets Manager are encrypted using an AWS Key Management Service (AWS KMS) customer master key (CMK). This rule is COMPLIANT if a secret is encrypted using an AWS KMS CMK. This rule is NON_COMPLIANT if a secret is encrypted using the default AWS KMS key.
Trigger type: Configuration changes
AWS Region: All supported AWS regions except China (Beijing), Canada West (Calgary), China (Ningxia) Region
How to Resolve Manually
You can resolve with this manually by heading to the Secrets Dashboard in AWS and selecting the key you want to re-congifure.
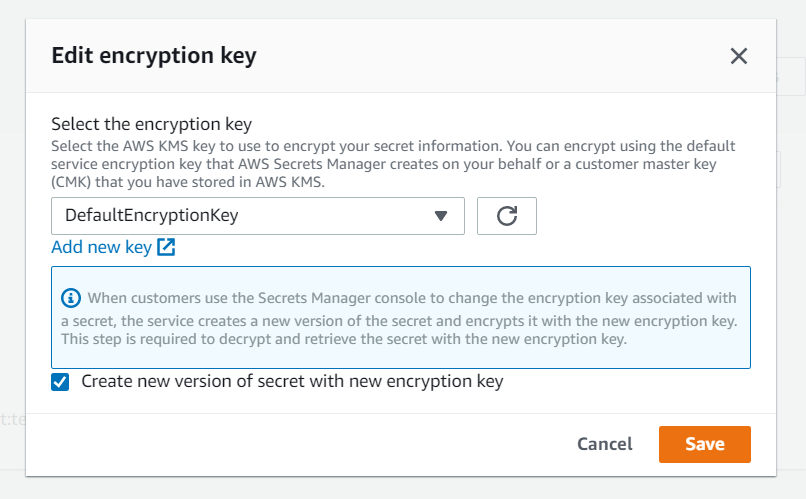
From here, head to the top "Actions" drop down tab and select Edit Encryption Key.
This will allow you to change the encryption key used to encrypt your secret information. You will need a customer managed key (CMK) which will already exist within your AWS KMS. Simply change from the DefaultEncryptionKey as seen below and select your own key, along with deciding if you want to create a new version of your secret with the newly selected encryption key. (You are probably going to want to do this)
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


