AWS - Financial Services
Fernando Honig
Last Update 2 jaar geleden
StackZone Financial Services Setup includes the necessary components enabled to support and build compliance according to this industry vertical.
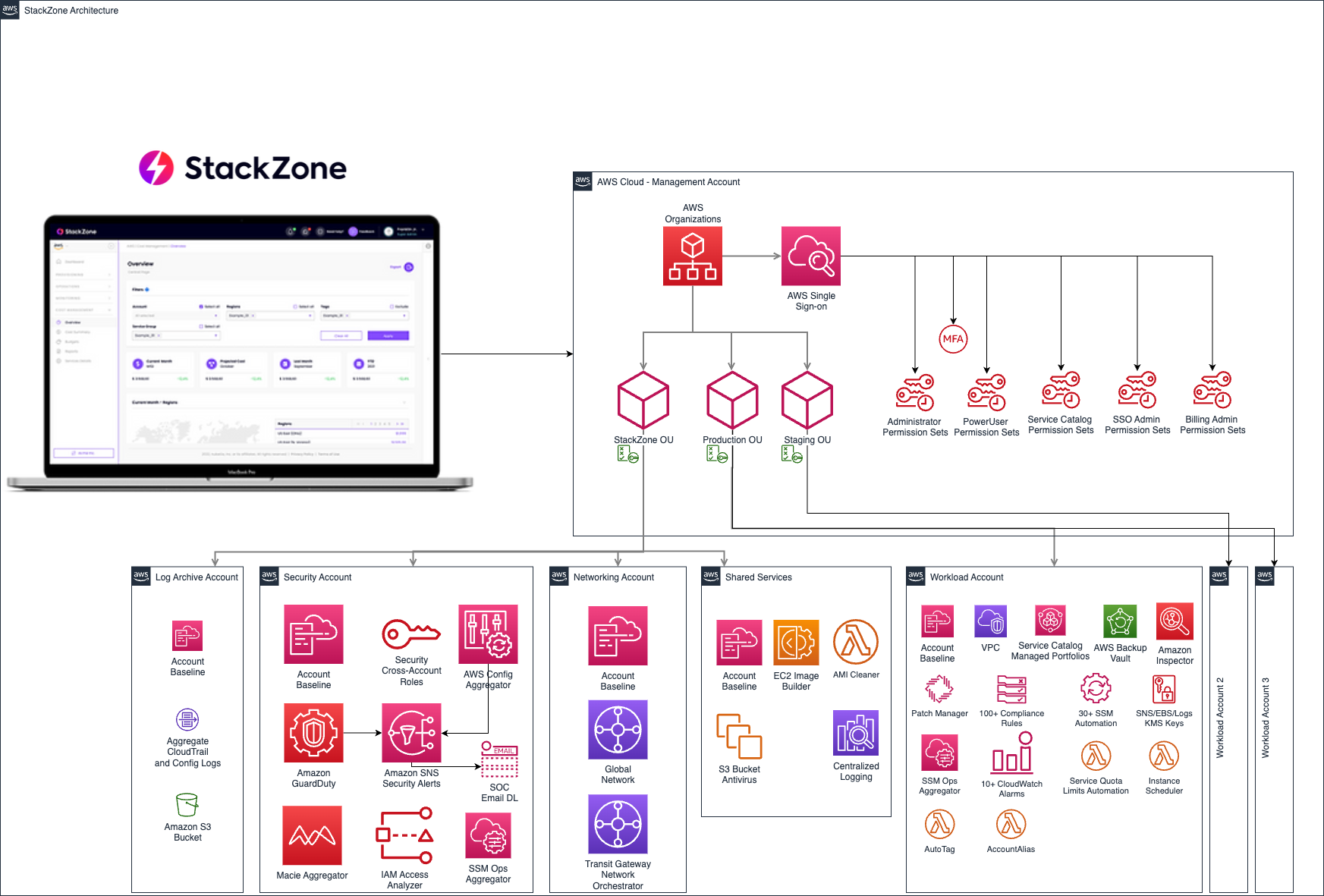
Components Created:
- Shared Services Account:
- Amazon VPC including Private and Public Subnets distributed in 2 availability zones in the primary region
- Log-Archive Account:
- Shared Amazon S3 Bucket with a lifecycle policy to store logs up to 7 years
- Security Account
- Aggregated SNS Security Topic (your email distribution list or account must be configured after the initial setup to start receiving the notifications)
- Central Amazon GuardDuty detector
- Central AWS Config global aggregator to visualise your compliance from a single place for your entire Organization
- Primary Account:
- Security Services Delegation to the Security Account
- Amazon S3 Storage Lens
- AWS License Manager
- AWS Systems Manager
- Amazon Macie
- AWS IAM Access Analyzer
- Custom AWS Budget Actions: Every 24 hours scans each account consumption and based on the tags applied to the account it could attach the stackzone-restrict-all-guardrails to avoid new resources to be launched.
- AWS Compute Optimizer: It enables this service in all accounts in the Organization
- Amazon Macie Aggregator: Configures Amazon Macie in all accounts and centralizes in the Security Account the results
- Service Control Policies
- Core OU Mandatory Preventive GuardRails
- Workloads OU Mandatory Preventive GuardRails
- StackZone Deny Preventive GuardRails
- StackZone Allow Enabled Regions GuardRails
- StackZone Allowed Tags Preventive GuardRails
- StackZone Deny Networking Preventive GuardRails
- StackZone PCI-DSS Services Only Preventive GuardRails
- StackZone SOC Services Only Preventive GuardRails
- Baseline Services (Applied to every account managed by StackZone)
- Lambda Helper (required Lambda functions for StackZone to operate)
- SNS Helper (required to forward Security SNS Notifications from all accounts to the Security Account)
- Key Management Service: Creates AWS KMS Keys for Amazon EBS Volumes, CloudWatch Logs and SNS Topics to be encrypted to maintain compliance.
- Amazon CloudTrail: Enables a multi-region, encrypted Trail in every account in the primary region that logs every action to the Amazon S3 Bucket in the Log-Archive Account and locally to an Amazon CloudWatch LogGroup.
- AWS Config:
- Creates an AWS IAM Role to run AWS Config Rules and Remediations.
- Enables AWS Config local aggregator in each account in the primary region
- Enables these global AWS Config rules in all accounts:
- StackZone-AccountPartofOrganizationsCheck
- StackZone-SSOEnabledCheck
- StackZone-CheckForRootMfa
- StackZone-CheckForIamPasswordPolicy
- StackZone-CheckForIAMUserMFA
- StackZone-AccessKeysRotated
- StackZone-IAMRootAccessKeyCheck
- StackZone-IAMGroupNoUsersCheck
- StackZone-IAMPolicyNoAdminCheck
- StackZone-IamUserGroupMembershipCheck
- Enables Automatic Remediation for:
- CheckForIamPasswordPolicyRemediation
- Require Lowercase
- Require Uppercase
- Require Symbols
- Require Numbers
- Minimum Password Length: 14
- Maximum Password Age: 90 days
- Password reuse prevention: 24
- Enables these regional AWS config Rules in all accounts:
- StackZone-CheckForBackupRecoveryPointEncrypted
- StackZone-CheckForBackupRecoveryPointManualDeletionDisabled
- StackZone-Config-RecoveryPointExpired-Check
- StackZone-CheckForESEncryptedAtRest
- StackZone-CheckForEFSEncrypted
- StackZone-CheckForEBSEncrypted
- StackZone-CloudWatchRetentionPeriod
- StackZone-CloudwatchLogGroupEncrypted
- StackZone-CloudtrailEnabledCheck
- StackZone-CloudTrailSecurityTrailEnabled
- StackZone-MultiRegionCloudTrailEnabled
- StackZone-CloudTrailLogFileValidationEnabled
- StackZone-CloudTrailEncryptionEnabled
- StackZone-GuardDutyEnabled
- StackZone-CheckForRdsEncryption
- StackZone-CheckForRdsPublicAccess
- StackZone-CheckForS3PublicRead
- StackZone-CheckForS3PublicWrite
- StackZone-VPCFlowLogsEnabled
- StackZone-VPCS3EndpointCheck
- StackZone-EIPAttachedCheck
- StackZone-EBSSnapshotPublicRestorableCheck
- StackZone-EC2InstanceNoPublicIP
- StackZone-ElasticsearchInVPCOnly
- StackZone-InstancesInVPC
- StackZone-RDSSnapshotsPublicProhibited
- StackZone-EKSSecretsEncryptedCheck
- StackZone-EKSEndpointNoPublicCheck
- StackZone-SecretsManagerRotationEnabledCheck
- StackZone-EC2StoppedInstancesCheck
- StackZone-EC2TerminationProtectionCheck
- StackZone-ECRScanOnPushCheck
- Enables Automatic Remediation for:
- StackZone-CloudWatchRetentionPeriod
- Set 14 days retention
- StackZone-CloudwatchLogGroupEncrypted
- Encrypts using the local KMS Key
- StackZone-CloudTrailLogFileValidationEnabled
- Enables LogFileValidation for CloudTrail
- StackZone-MultiRegionCloudTrailEnabled
- Enables MultiRegion for CloudTrail
- StackZone-VPCFlowLogsEnabled
- Enables VPCFlowLogs to all VPCs
- StackZone-VPCS3EndpointCheck
- Creates a VPC S3 Endpoint to all VPCs
- Amazon CloudWatch alarms:
- Amazon CloudTrail changes alarm
- AWS Console failed sign-in alarm
- AWS IAM Policy changes alarm
- AWS IAM root login alarm
- AWS Console sign-in no MFA alarm
- Amazon Macie findings alarm
- AWS IAM Access Analyzer findings alarm
- AWS Service Catalog:
- Creates Network Portfolio with VPC and Endpoints products
- Creates Security Portfolio with KMS and WAF products
- EC2 - Isolation:
- Enables automatic ec2 isolation based on a pre-defined tag key and value; Key: ec2-isolation Value: True
- EBS Optimizer:
- Enables automatic conversion from gp2 to gp3 volumes using a pre-defined tag key and value; Key: EBSOptimizer Value: True
Average Time to deploy: 3 hours (including the creation of all AWS core-accounts)


