AWS - SaaS (AWS SSB)
Fernando Honig
Last Update 2 jaar geleden
StackZone SaaS Setup includes the necessary components enabled to prevent, detect and in some cases remediate high risk items defined by the AWS Startup Security Baseline (AWS SSB) and build compliance according to AWS Prescriptive Guidance.
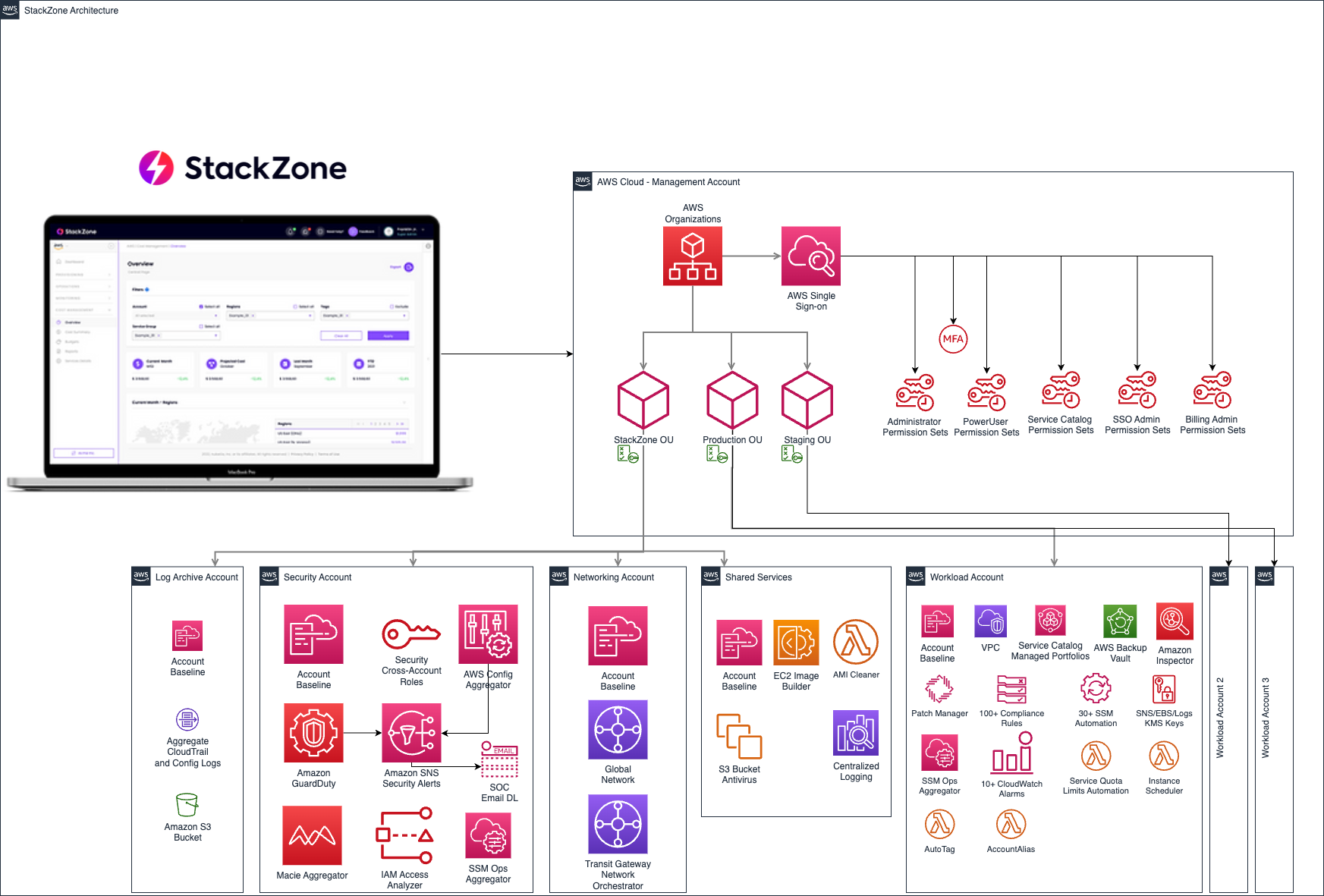
Components Created:
For the following Controls defined by AWS, we have tailored different solutions:
- ACCT.02
- Enable Check for Root Access Keys Rule
- ACCT.03
- Enable Check for IAM User Groups with no Users Rule
- ACCT.04
- Enable Check for IAM Users with no policies Rule
- Enable Check for IAM Policies No Inline Rule
- ACCT.05
- Enable Check for IAM User MFA and IAM User Console MFA
- Enable Check for Root MFA Rule
- Enable Check for Root Hardware MFA Rule
- ACCT.06
- Enable Check for IAM Password Policy Rule and Remediation
- ACCT.07
- Enable CloudTrail Enabled Rule
- Enable CloudTrail Security Trail Rule
- Enable CloudTrail Multi-Region Rule and Remediation
- Enable CloudTrail Log-File Validation Rule and Remediation
- Enable CloudTrail CloudWatch Logs Enabled Rule
- Enable CloudTrail Encryption Enable Rule
- Enable Centralized S3 Bucket to store up to 7 years of CloudTrail Logs
- ACCT.08
- Enabled Check for S3 Public Read Rule
- Enabled Check for S3 Public Write Rule
- Enabled Check for S3 Account Level Public Access Rule
- ACCT.09
- Remove all Default VPCs in all Regions
- Enable Check for EIP Attached Rule
- Enable Check for EC2 Stopped Instances Rule
- Enable Check for EBS Volumes in use Rule
- ACCT.10
- Enable AWS Budgets for $1,000USD Monthly in all Accounts
- ACCT.11
- Enable GuardDuty in the Security Account and Remediations to block offender IP in the VPC NACL Subnets
- ACCT.12
- Enable CloudWatch Alarm for CloudTrail changes
- Enable CloudWatch Alarm for VPC changes
- Enable CloudWatch Alarm for Root Login attempts
- Enable CloudWatch Alarm for Trusted Advisor events
- WKLD.01
- Enable Check for IAM User Group membership Rule
- Enable Check for Amazon EC2 Instance Profile Attached Rule
- WKLD.03
- Create AWS Managed KMS Keys for EBS Volumes, CloudWatch Logs, SNS Topics and AWS Backup Vaults shared with the entire Organization.
- Enable Check for KMS Key not scheduled for deletion Rule
- Enable Check for KMS Key rotation Enabled Rule
- Enable Check for Secrets Manager using KMS Key Rule
- Enable Check for Secrets Manager rotation Enabled Rule
- WKLD.04
- Enable Check for EKS Secrets Encrypted Rule
- Enable Check for CodeBuild AWS Credentials Environment Variables Rule
- WKLD.06
- Enable Check for Amazon EC2 SSM Managed Rule
- Enable Check for Amazon Systems Manager Associations Rule
- Enable SSM Associations using Tags for EC2 Resources (gather-inventory, cloudwatch-agent update and query-scan-patches)
- WKLD.07
- Enable CloudTrail S3 Events
- Enable Check for CloudTrail S3 Events Rule
- WKLD.08
- Enable Check for EBS Encryption Rule and Remediation using EBS KMS Key in all Accounts and Regions
- WKLD.09
- Enable Check for RDS Encryption Rule
- Enable Check for RDS Snapshots Encrypted Rule
- WKLD.10
- Enable Check for EC2 Instances in VPC Rule
- Enable Check for AWS Lambda Functions in VPC Rule
- Enable Check for Amazon RDS not public Rule
- Enable Check for Subnet Auto-Assign Public Ip Disabled Rule
- Enable Check for EC2 Instances Public Ip Disabled Rule
- WKLD.11
- Enable Check for Restricted Common Ports Rule (20/21/3389/3306/4333)
- Enable Check for VPC Security Groups open to specific ports (80,443,53)
- Enable Check for VPC Default Security Group closed Rule and Remediation
- WKLD.12
- Enable Check for VPC S3 Endpoint Rule and Remediation
- Enable Check for VPC DynamoDB Endpoint Rule and Remediation
- WKLD.13
- Enable Check for ELB TLS HTTPS Listener only Rule
- Enable Check for CloudFront Viewer https Policy Rule
- Enable Check for OpenSearch https required Rule
- Enable Check for ALB http to https redirect
- Enable Check for RedShift require tls-ssl Rule
- WKLD.14
- Enable Check for WAFv2 Enabled Rule
- Enable Check for ALB WAFv2 Enabled Rule
- Enable Check for CloudFront associated with WAFv2 Rule
- WKLD.15
- StackZone is managed fully with CloudFormation, StackSets and CodePipeline
Average Time to deploy: 3 hours (including the creation of all AWS core-accounts)


