AWS - SOC2
Eduardo Van Cauteren
Last Update 2 tahun yang lalu
StackZone SOC2 Setup includes the necessary components enabled to support and build compliance according to this industry vertical.
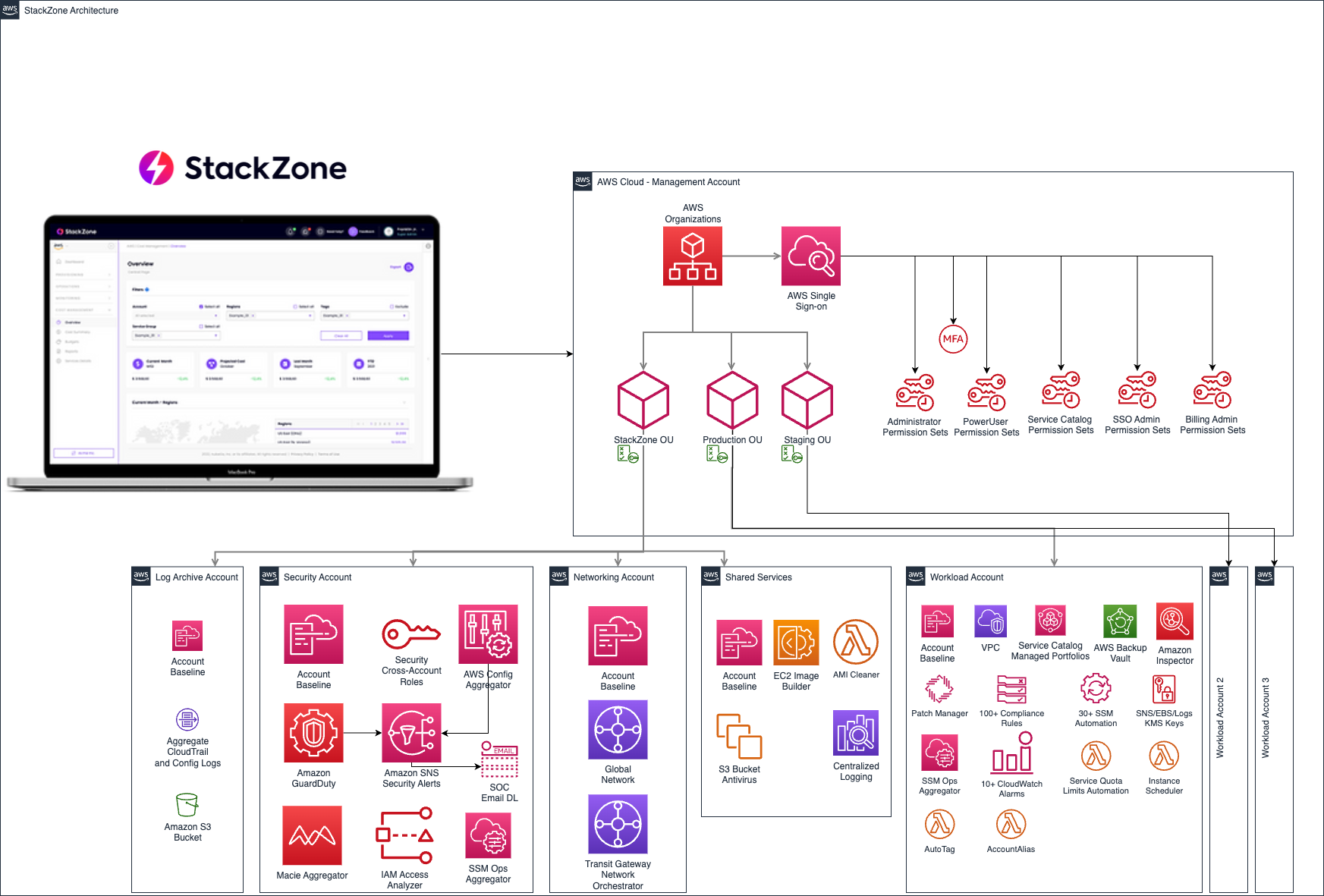
Components Created:
- Shared Services Account:
- Amazon VPC including Private and Public Subnets distributed in 2 availability zones in the primary region
- Log-Archive Account:
- Shared Amazon S3 Bucket with a lifecycle policy to store logs up to 7 years
- Security Account:
- Central Amazon GuardDuty detector
- GuardDuty Remediation (NACL Retention (720 h))
- Central AWS Config global aggregator to visualize your compliance from a single place for your entire Organization
- Primary Account:
- AWS Compute Optimizer
- Security Services Delegation to the Security Account
- Amazon S3 Storage Lens
- AWS License Manager
- AWS Systems Manager
- Amazon Macie
- AWS IAM Access Analyzer
- Service Control Policies:
- Core OU Mandatory Preventive GuardRails
- Non Core Mandatory Preventive Guardrails
- StackZone Deny Mandatory Preventive Guardrails
- StackZone Allowed Regions Preventive Guardrails
- StackZone Tagging Preventive Guardrails
- StackZone Networking Preventive Guardrails
- StackZone HIPAA Preventive Guardrails
- StackZone PCI Preventive Guardrails
- StackZone SOC Preventive Guardrails
- StackZone Restrict All Guardrails
- StackZone Machine Learning Ops Guardrails
- Baseline Services (Applied to every account managed by StackZone):
- Lambda Helper (required Lambda functions for StackZone to operate)
- SNS Helper (required to forward Security SNS Notifications from all accounts to the Security Account)
- Key Management Service: Creates AWS KMS Keys for Amazon EBS Volumes, CloudWatch Logs and SNS Topics to be encrypted to maintain compliance.
- Amazon CloudTrail: Enables a multi-region, encrypted Trail in every account in the primary region that logs every action to the Amazon S3 Bucket in the Log-Archive Account and locally to an Amazon CloudWatch LogGroup.
- AWS Config:
- Creates an AWS IAM Role to run AWS Config Rules and Remediations.
- Enables AWS Config local aggregator in each account in the primary region.
- Enables these global AWS Config rules in all accounts:
- No Inline Policy
- IAM Policy no statements with full access
- Root MFA Enabled
- IAM Password Policy
- IAM User MFA Enabled
- IAM User Console MFA Enabled
- IAM User Unused Credential
- IAM Access keys Rotated
- IAM Root Access Key Check
- IAM User No Policies Attached
- IAM User Group Has No Users
- IAM Policy No Admin Permissions
- IAM User Group Membership Check
- Enables Automatic Remediation for: AM Password Policy Remediation
- Require Uppercase
- Require Lowercase
- Require Symbols
- Require Numbers
- Min Password Length, Password Re-Use Prevention, Max Password Age
- Enables these regional AWS config rules in all accounts:
- AWS Key Management Service
- CMK Not Scheduled For Deletion
- CMK Key Rotation Enabled
- Amazon GuardDuty
- GuardDuty Enabled
- PCI-DSS Compliance
- EC2 Instance No Public IP
- OpenSearch HTTPS Required
- EC2 Instances in VPC
- VPC Security Group Open to Authorized Ports
- EKS Secrets Encrypted
- Secrets Manager Rotation Enabled
- Secrets Manager Using CMK
- Amazon EC2 AutoScaling Group
- AutoScaling Group Using ELB Healthcheck
- Amazon RDS
- RDS Encryption Enabled
- RDS Public Access Disabled
- RDS Snapshots Encrypted
- Amazon EBS
- EBS Attached Volumes Encrypted
- EBS Volumes Encrypted
- Enables Automatic Remediation for: EBS Volumes Encrypted Remediation
- Amazon S3
- S3 Public Read Prohibited
- S3 Public Write Prohibited
- S3 Bucket Server Side Encryption
- S3 Account Level Public Access Prohibited
- S3 Bucket Logging Enabled
- S3 Public Read Prohibited Remediation
- S3 Public Write Prohibited Remediation
- S3 Bucket Server Side Encryption Remediation
- Amazon EC2
- EC2 Instance Managed by SSM
- EC2 Instance Association Compliance Status
- EC2 Stopped Instance
- EC2 Instance Profile Attached
- Amazon Redshift
- Cluster Require TLS SSL
- Network
- VPC Subnet Auto Assign Public IP Disabled
- VPC Flowlogs Enabled
- VPC Security Group Restricted SSH Policy
- VPC Security Group Restricted Common Ports Policy
- VPC S3 Gateway Endpoint Enabled
- VPC DynamoDB Gateway Endpoint Enabled
- VPC Default Security Group Closed
- No Default VPC Check
- VPC Elastic IP Attached
- Enables Automatic Remediation for:
- VPC Flowlogs Enabled Remediation
- VPC Default Security Group Closed
- VPC S3 Gateway Endpoint Enabled Remediation
- VPC DynamoDB Gateway Endpoint Enabled Remediation
- AWS CloudFront
- CloudFront Associated with WAF
- CloudFront HTTPS Viewer Policy
- AWS CloudTrail
- CloudTrail Enabled
- CloudTrail Security Trail Enabled
- Multi Region CloudTrail Enabled
- CloudTrail Log File Validation Enabled
- CloudTrail Amazon CloudWatch Logs Enabled
- CloudTrail Encryption Enabled
- CloudTrail S3 Dataevents Enabled
- Enables Automatic Remediation for:
- CloudTrail Log File Validation Remediation
- Multi Region CloudTrail Remediation
- Amazon CloudWatch:
- CloudWatch Alarms
- Amazon VPC Change Alarm
- AWS CloudTrail Change Alarm
- AWS Console Root Login Alarm
- AWS Console Sign-In No MFA Alarm
- CloudWatch Event Rules
- AWS Trusted Advisor Event Rule
- AWS Backup & Restore
- AWS Billing:
- AWS Budgets
- AWS SSM Associations
- Update SSM Agent
- Query Scan Patches
- Gather Inventory
- Amazon EC2 Isolation

