AWS - Well Architected Framework
Fernando Honig
Last Update a year ago
StackZone AWS Well Architected Blueprint Setup includes the necessary components enabled to remediate up to 43% (as of time of writing this article) of the High Risk Items found in a Well Architected Review
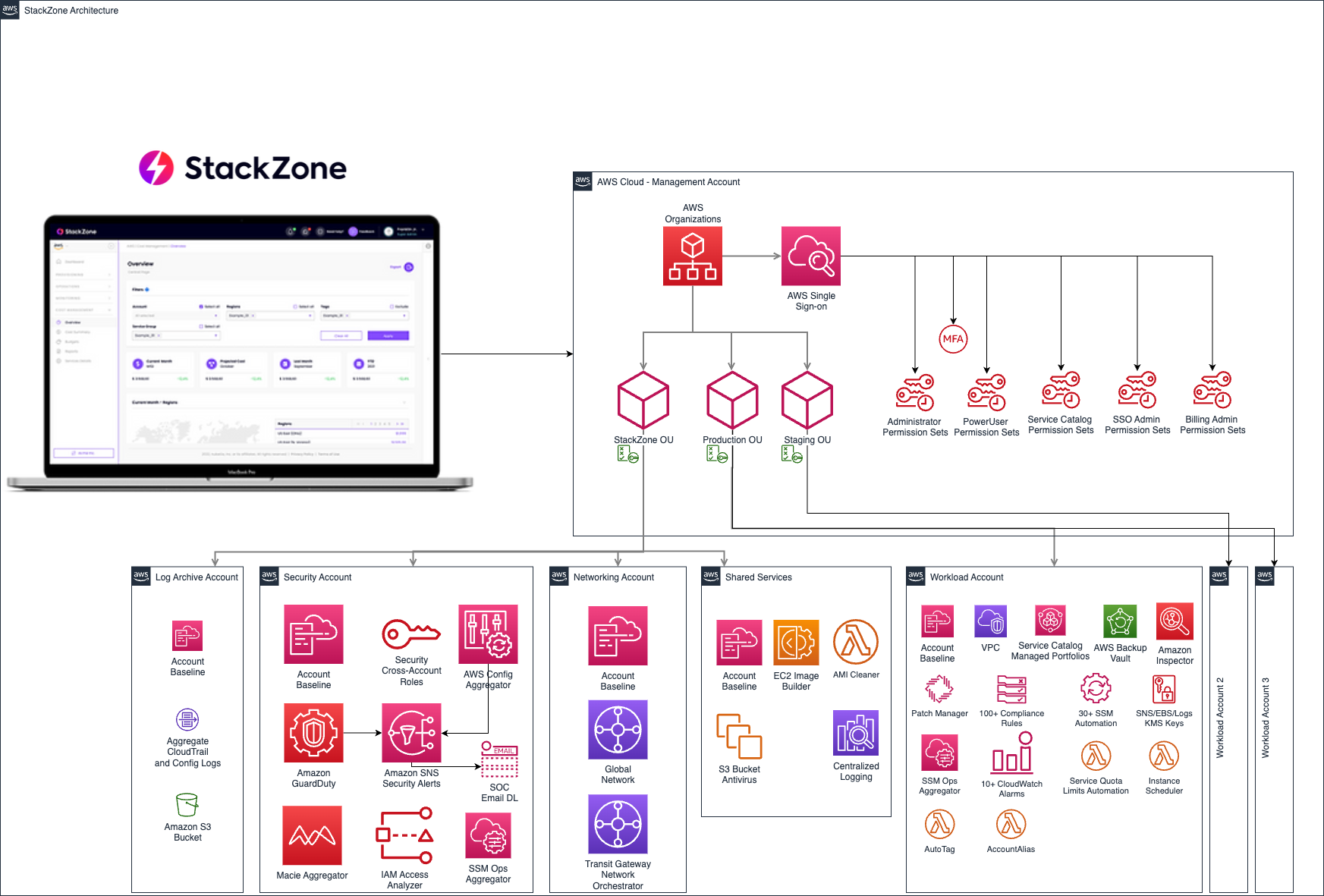
Components Created:
- Shared Services Account:
- Amazon VPC including Private and Public Subnets distributed in 2 availability zones in the primary region
- Log-Archive Account:
- Shared Amazon S3 Bucket with a lifecycle policy to store logs up to 7 years
- Security Account
- Aggregated SNS Security Topic (your email distribution list or account must be configured after the initial setup to start receiving the notifications)
- Central Amazon GuardDuty detector
- Central AWS Config global aggregator to visualize your compliance from a single place for your entire Organization
- Primary Account:
- Security Services Delegation to the Security Account
- AWS Security Hub (if enabled)
- Amazon S3 Storage Lens
- AWS License Manager
- AWS Systems Manager
- Amazon Macie
- AWS IAM Access Analyzer
- Custom AWS Budget Actions: Every 24 hours scans each account consumption and based on the tags applied to the account it could attach the stackzone-restrict-all-guardrails to avoid new resources to be launched.
- AWS Compute Optimizer: It enables this service in all accounts in the Organization
- Amazon Macie Aggregator: Configures Amazon Macie in all accounts and centralizes in the Security Account the results
- Service Control Policies
- Core OU Mandatory Preventive GuardRails
- Workloads OU Mandatory Preventive GuardRails
- StackZone Deny Preventive GuardRails
- StackZone Allow Enabled Regions GuardRails
- StackZone Allowed Tags Preventive GuardRails
- StackZone Deny Networking Preventive GuardRails
- Baseline Services (Applied to every account managed by StackZone)
- Lambda Helper: (required Lambda functions for StackZone to operate)
- SNS Helper: (required to forward Security SNS Notifications from all accounts to the Security Account)
- Key Management Service: Creates AWS KMS Keys for Amazon EBS Volumes, CloudWatch Logs and SNS Topics to be encrypted to maintain compliance.
- Amazon CloudTrail: Enables a multi-region, encrypted Trail in every account in the primary region that logs every action to the Amazon S3 Bucket in the Log-Archive Account and locally to an Amazon CloudWatch LogGroup.
- AWS Config:
- Creates an AWS IAM Role to run AWS Config Rules and Remediations.
- Enables AWS Config local aggregator in each account in the primary region
- Enables these global AWS Config rules in all accounts:
- StackZone-AccountPartofOrganizationsCheck
- StackZone-SSOEnabledCheck
- StackZone-IamNoInlinePolicyCheck
- StackZone-CheckForRootMfa
- StackZone-CheckForIamPasswordPolicy
- StackZone-CheckForIAMUserMFA
- StackZone-CheckForIAMUserConsoleMFA
- StackZone-IAMUserUnusedCredentialCheck
- StackZone-AccessKeysRotated
- StackZone-IAMRootAccessKeyCheck
- StackZone-RootAccountHardwareMFAEnabled
- StackZone-IAMUserNoPoliciesCheck
- StackZone-IAMGroupNoUsersCheck
- StackZone-IAMPolicyNoAdminCheck
- StackZone-IamUserGroupMembershipCheck
- Enables Automatic Remediation for:
- StackZone-CheckForIamPasswordPolicy
- Require Lowercase
- Require Uppercase
- Require Symbols
- Require Numbers
- Minimum Password Length: 14
- Maximum Password Age: 90 days
- Password reuse prevention: 24
- StackZone-AccessKeysRotated
- StackZone-IamNoInlinePolicyCheck
- StackZone-CheckForIAMUserConsoleMFA
- Enables these regional AWS config Rules in all accounts:
- StackZone-CheckForEFSProtectedbyBackupPlan
- StackZone-CheckForEBSProtectedbyBackupPlan
- StackZone-CheckForEC2ProtectedbyBackupPlan
- StackZone-CheckForAuroraProtectedbyBackupPlan
- StackZone-CheckForDynamoDBProtectedbyBackupPlan
- StackZone-CheckForFSxProtectedbyBackupPlan
- StackZone-CheckForRDSProtectedbyBackupPlan
- StackZone-CheckForBackupRecoveryPointEncrypted
- StackZone-CheckForBackupRecoveryPointManualDeletionDisabled
- StackZone-Config-RecoveryPointExpired-Check
- StackZone-CheckForESEncryptedAtRest
- StackZone-CheckForEFSEncrypted
- StackZone-CheckForEBSEncrypted
- StackZone-CloudWatchRetentionPeriod
- StackZone-CloudwatchLogGroupEncrypted
- StackZone-CloudFormationStackDriftDetection
- StackZone-CloudtrailEnabledCheck
- StackZone-CloudTrailSecurityTrailEnabled
- StackZone-MultiRegionCloudTrailEnabled
- StackZone-CloudTrailLogFileValidationEnabled
- StackZone-CloudTrailEncryptionEnabled
- StackZone-GuardDutyEnabled
- StackZone-CheckForRdsEncryption
- StackZone-CheckForRdsPublicAccess
- StackZone-RDSSnapshotsEncrypted
- StackZone-RDSBackupEnabled
- StackZone-RdsEnhancedMonitoringEnabled
- StackZone-RDSInstanceDeletionProtectionEnabled
- StackZone-RDSMultiAZEnabled
- StackZone-CheckForRdsMinorVersionUpgrade
- StackZone-CheckForS3PublicRead
- StackZone-CheckForS3PublicWrite
- StackZone-SubnetAutoAssignPublicIPDisabledCheck
- StackZone-HttpToHttpsRedirectionCheck
- StackZone-VPCFlowLogsEnabled
- StackZone-VPCS3EndpointCheck
- StackZone-VPCDynamoDBEndpointCheck
- StackZone-EIPAttachedCheck
- StackZone-EBSSnapshotPublicRestorableCheck
- StackZone-EC2InstanceNoPublicIP
- StackZone-ElasticsearchInVPCOnly
- StackZone-InstancesInVPC
- StackZone-RDSSnapshotsPublicProhibited
- StackZone-EKSSecretsEncryptedCheck
- StackZone-EKSEndpointNoPublicCheck
- StackZone-SecretsManagerRotationEnabledCheck
- StackZone-ApiGwXRayEnabled
- StackZone-EC2SSMManagedCheck
- StackZone-EC2StoppedInstancesCheck
- StackZone-Ec2Imdsv2Check
- StackZone-DesiredInstanceTypeCheck
- StackZone-EC2TerminationProtectionCheck
- StackZone-ECRScanOnPushCheck
- Enables Automatic Remediation for:
- StackZone-CloudWatchRetentionPeriod
- Set 14 days retention
- StackZone-CloudwatchLogGroupEncrypted
- Encrypts using the local KMS Key
- StackZone-CloudTrailLogFileValidationEnabled
- Enables LogFileValidation for CloudTrail
- StackZone-MultiRegionCloudTrailEnabled
- Enables MultiRegion for CloudTrail
- StackZone-VPCFlowLogsEnabled
- Enables VPCFlowLogs to all VPCs
- StackZone-VPCS3EndpointCheck
- Creates a VPC S3 Endpoint in all VPCs
- StackZone-VPCDynamoDBEndpointCheck
- Creates a VPC DynamoDB Endpoint in all VPCs
- StackZone-EC2SSMManagedCheck
- Attaches an IAM Role to enable SSM Management and installs SSM-Agent to EC2 Instances.
- StackZone-ECRScanOnPushCheck
- Enables Scan On Push to all Amazon ECR repositories
- Amazon CloudWatch alarms:
- Amazon EC2 Instance Change alarm
- Amazon EC2 Large Instance Change alarm
- Amazon CloudTrail changes alarm
- AWS Console failed sign-in alarm
- AWS IAM Policy changes alarm
- AWS IAM root login alarm
- Reject SSH count alarm
- AWS Console sign-in no MFA alarm
- AWS Trusted Advisor rule alarm
- Amazon Macie findings alarm
- Amazon S3 policy changes alarm
- AWS IAM Access Analyzer findings alarm
- Amazon EFS unencrypted alarm
- Amazon EBS changes alarm
- Amazon CloudWatch Auto-Create alarms
- It creates CPU/Disk/Memory Amazon CloudWatch Alarms when an EC2 instance is tagged with Key: cw-auto-alarm. Thresholds are pre-defined and can be changed afterwards.
- AWS Backup Solution
- It creates an AWS Backup encrypted vault and backs up every supported resource if there is a tag-key backup and the value could be daily/weekly/monthly or any combination of these.
- AMI Deprecation checker
- It monitors every 24 hours AMIs created and checks for the DeprecationDate parameter. If the deprecation date value is within 14 days, it creates an OpsItem in AWS Systems Manager for you to fix it.
- Amazon Inspector
- It enables Amazon Inspector assessments based on the CVE rule package. Every EC2 Instance tagged with a Key: Inspector and the Value: true will be assessed weekly on Saturday midnight UTC.
- Patch Management
- It creates 2 schedules to run Patch Management in your EC2 Instances. First Schedule runs on Tuesday midnight UTC and the second one on Wednesday midnight. You can tag your EC2 Instances with Key AutoPatchDev for Tuesday and AutoPatchProd for Wednesday. On both cases the tag Value must be true
- Instance Scheduler Solution
- It configures Instance Scheduler solution and creates 2 custom schedules. office-hours-uk (8-18 Mon-Fri UTC) and office-hours-us-pacific (8-18 Mon-Fri US/Pacific). To enable it you must tag your EC2 Instances with tag-key Schedule and in the tag-value use the schedule name. E.g: office-hours-uk
- AWS Service Catalog:
- Creates Network Portfolio with VPC and Endpoints products
- Creates Application Portfolio with AWS Load Testing and Jenkins Master products
- Creates Security Portfolio with KMS and WAF products
- EC2 - Isolation:
- Enables automatic ec2 isolation based on a pre-defined tag key and value; Key: ec2-isolation Value: True
- S3 Replication:
- Replicates any bucket tagged with Key: S3Replication and the Value must be the destination bucket name. E.g.: my-bucket-123
- EBS Optimizer:
- Enables automatic conversion from gp2 to gp3 volumes using a pre-defined tag key and value; Key: EBSOptimizer Value: True
Average Time to deploy: 6 hours (including the creation of all AWS accounts)


