AWS Config Rule: CloudFront Access Logs Enabled
CLOUDFRONT_ACCESSLOGS_ENABLED
Ryan Ware
Last Update há um ano
Description: Checks if Amazon CloudFront distributions are configured to capture information from Amazon Simple Storage Service (Amazon S3) server access logs. This rule is NON_COMPLIANT if a CloudFront distribution does not have logging configured.
Trigger type: Configurational Changes
AWS Region: Only available in US East (N. Virginia) Region
How to Resolve Manually
Once you have created your CloudFront Distribution from the AWS Console or AWS CLI, you will see within the main tab of settings under "General" these options pictured below. What you will notice is that you may have logging "off" as a default configuration. As it stands, this CloudFront Distribution will be marked as NON_COMPLIANT by this particular AWS Config Rule.
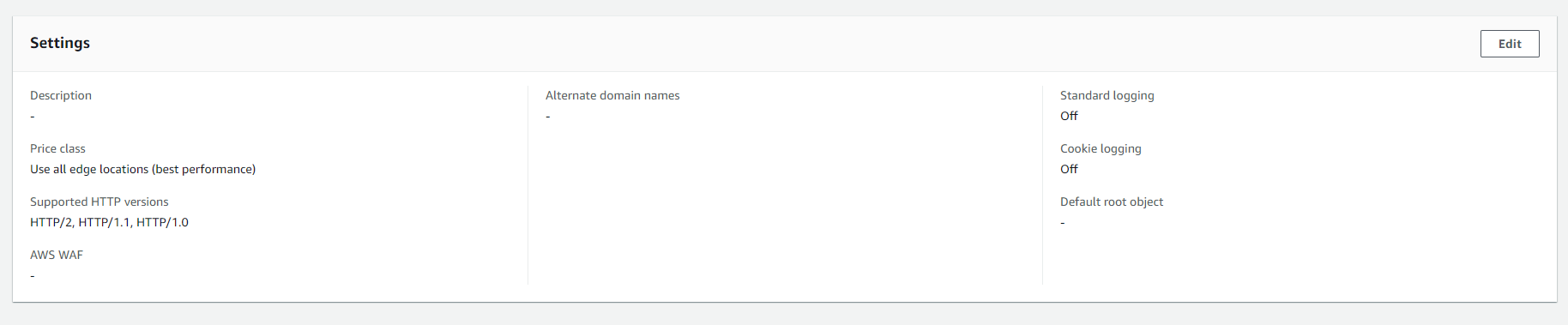
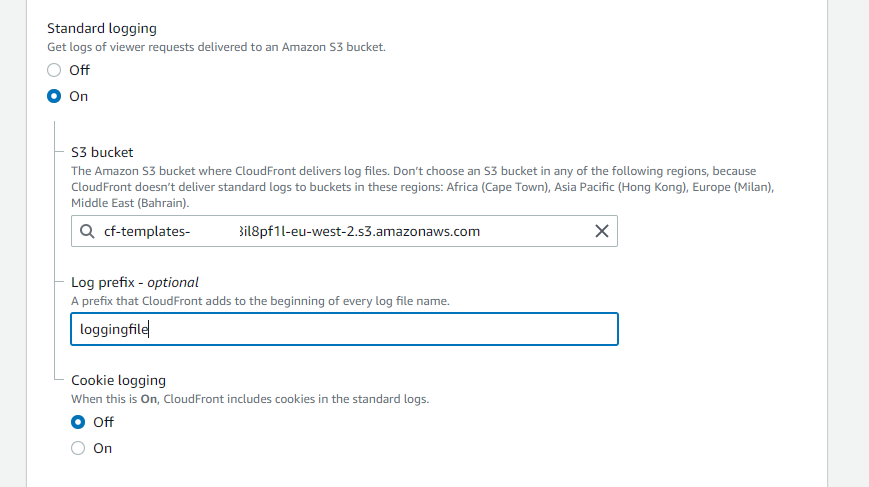
In order to resolve this, we will have to configure logging for this CloudFront Distribution. Click Edit in the above image and scroll down to find standard logging.
Standard Logging will need to be toggled "on" and then you can select a logging S3 Bucket for this CloudFront Distribution. You can also optionally enable cookie logging but this has no bearing on the compliance status of this particular AWS Config Rule.
How to Resolve with StackZone
StackZone can automatically resolve your non-compliant CloudFront Distribution Access Logs by running an automation script to enable logging and define a S3 Bucket to store them out.
To enable this remediation, within the StackZone console head on over to Provisioning > Baseline Services > AWS Config Rules Regional > AWS CloudFront, and enable the CloudFront Access Logs Enabled Remediation.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


