AWS Config Rule: CloudFront Origin Access Identity Enabled
CLOUDFRONT_ORIGIN_ACCESS_IDENTITY_ENABLED
Ryan Ware
Last Update 2 jaar geleden
Description: Checks if Amazon CloudFront distribution with S3 Origin type has Origin Access Identity (OAI) configured. The rule is NON_COMPLIANT if the CloudFront distribution is backed by S3 and any of S3 Origin type is not OAI configured. The rule is NON_COMPLIANT if the origin is not an S3 bucket; the rule does not return NOT_APPLICABLE if the origin is not as S3 bucket.
Trigger type: Configuration changes
AWS Region: Only available in US East (N. Virginia) Region
How to Resolve Manually
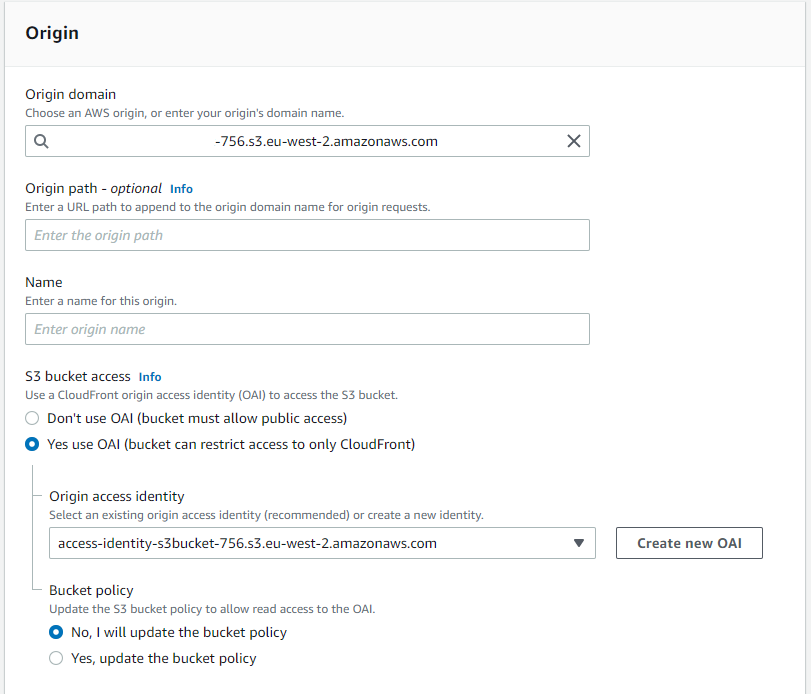
If you have a CloudFront Distribution which uses an Amazon S3 Bucket as it's origin domain, we can either use Origin Access Identity (OAI) or not, which will mean your S3 Bucket must allow public access. This AWS Config Rule will check if we have OAI enabled. So let's look at how we can enable this.
If you don’t use an OAI, your S3 bucket must allow public access. If you don’t want your S3 bucket to allow public access, you can use an OAI. With an OAI, CloudFront sends authenticated requests to your S3 bucket. This means you can block public access to your S3 bucket while still allowing CloudFront to get objects from the bucket.
When we select "Yes use OAI" - some additional configuration options appear. You will need to select or create a new OAI as well as set the option to either update the Bucket Policy manually or allow AWS to edit this policy.
It's up to you which option you choose, but you must allow the new OAI to access the Bucket from the Bucket Policy perspective, or the authorization will fail.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


