AWS Config Rule: CloudFront No Deprecated SSL Protocols
CLOUDFRONT_NO_DEPRECATED_SSL_PROTOCOLS
Ryan Ware
Last Update há 2 anos
Description: Checks if CloudFront distributions are using deprecated SSL protocols for HTTPS communication between CloudFront edge locations and custom origins. This rule is NON_COMPLIANT for a CloudFront distribution if any ‘OriginSslProtocols’ includes ‘SSLv3’.
Trigger type: Configuration changes
AWS Region: Only available in US East (N. Virginia) Region
How to Resolve Manually
In order to resolve this setting manually, we will need to head on over to the CloudFront dashboard within the AWS Console.
You will need to select the correct CloudFront Distribution and check the Protocols setting applied to the CloudFront Origin.
Here, the Protocol settings allow you to choose the minimum SSL/TLS protocol that you want CloudFront to use when it establishes an HTTPS connection to the origin. AWS recommends that you choose the latest TLS protocol that your origin supports.
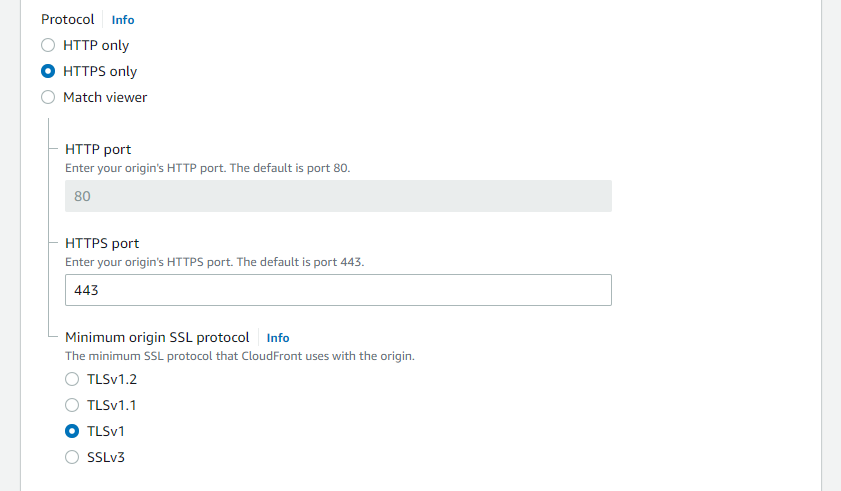
By choosing TLSv1 from this list we are telling CloudFront that we will accept TLSv1, TLSv1.1 and TLSv1.2 SSL protocols only. It will not accept SSLv3 protocols.
The AWS Config Rule is NON_COMPLIANT if this setting is allowing the SSLv3 protocol. By Default the origin should be set to TLSv1 - however it should always be checked incase this is not set by default.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


