AWS Config Rule: CloudWatch LogGroup Data Protection Check
CLOUDWATCH_LOGGROUP_DATA_PROTECTION
Ryan Ware
Last Update één jaar geleden
Description: A Config rule that checks whether Amazon CloudWatch LogGroup DataProtection is set. The rule is NON_COMPLIANT if the dataprotection is not ACTIVATED.
Trigger type: Periodic
AWS Region: All supported AWS regions.
How to Resolve Manually
To resolve this manually, you will need to ensure that your CloudWatch Log Groups are set with data protection setting to activated. This means you will need a Data Protection policy defined and also define what data identifiers we want to audit from the CloudWatch Log Group(s)
Data Protection from AWS:
1. Select which data identifiers will be audited such as Credit Card Numbers or IAM Access Keys.
2. Choose where to send findings when data that matches the selected data identifiersis sent.
3. Configure which data identifiers should be masked.
Let's take a look at an example CloudWatch Logs Data Protection Policy:

Now that we have this constructed to capture the specific fields, we can activate this for the current CloudWatch Log Group.
After pressing Activate, we can see from the Data Protection tab of this specific Log Group, that we have an Active status and we can see further details of this policy in place such as a count from AWS for the amount of times the specific data identifiers have been found within your chosen CloudWatch Log Group.
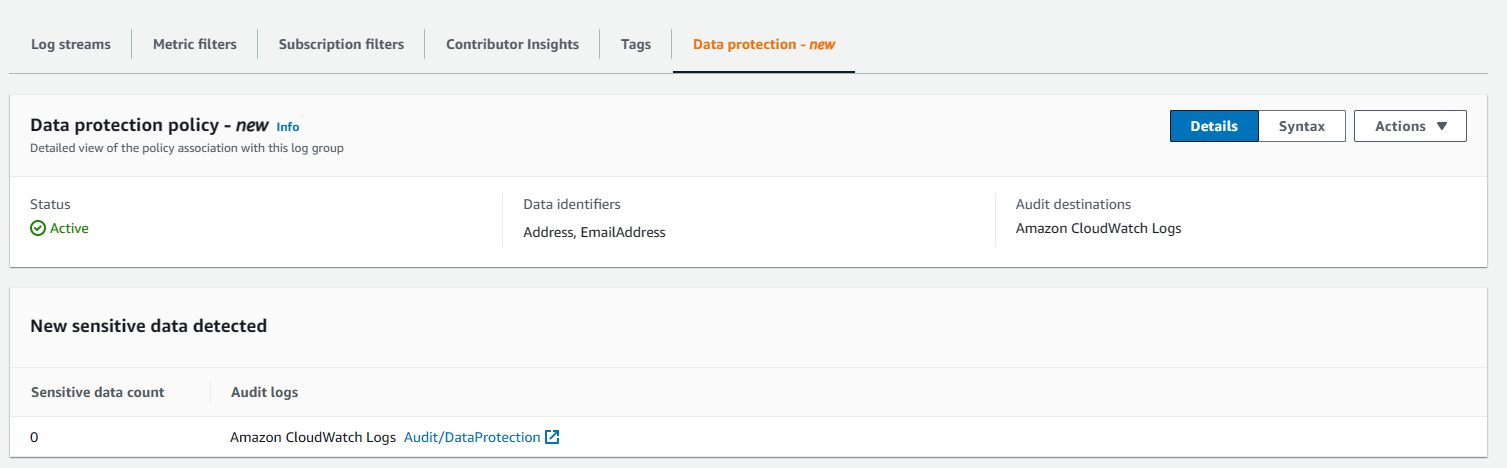
This is how you can ensure compliance for your CloudWatch Log Group data protection policy AWS Config Rule
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


