AWS IAM: Password Policy
Identity and Access Management: How To Guide
Ryan Ware
Last Update 3 jaar geleden
The Password Policy you can define boundaries for AWS IAM user's Passwords at the account level. Here you can toggle options to make it more complex, such as requiring Uppercase and Lowercase characters, or even Numbers and Symbols to be mandatory parts of your IAM password policy. Having a complex IAM Password policy mitigates against letting your users have week passwords which can potentially be a security risk.
AWS IAM: Default Password Policy
AWS defines a password policy per AWS Account by default which covers the type of password an IAM user can set. This is quite basic and should be strengthened if possible. In this guide we will show you how to do this.
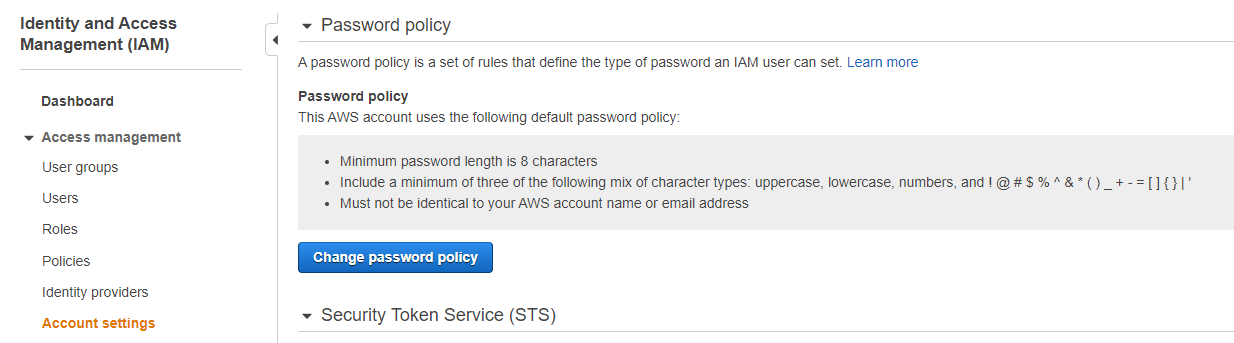
The default password policy has the following attributes;
- Minimum password length is 8 characters
- Include a minimum of three of the following mix of character types: uppercase, lowercase, numbers, and ! @ # $ % ^ & * ( ) _ + - = [ ] { } | '
- Must not be identical to your AWS account name or email address
Changing your AWS IAM Password Policy
To change your default AWS IAM Password Policy, head on over to the Identity and Access Management (IAM) dashboard within the AWS Console.
From here, choose Account Settings from the left hand side tab under the Access management header.
You can browse the current Password policy along with changing this policy via the blue button as shown below
Choosing a New AWS IAM Password Policy
You may choose a new AWS IAM Password Policy which will define complexity requirements and set a mandatory rotation period for all AWS IAM users. You can read more on these within AWS' official documentation here.
- Enforce minimum password length
This will mean any passwords need to be as long, or longer, than the number you provide here in your new policy
- Require at least one uppercase letter from Latin alphabet (A-Z)
- Require at least one lowercase letter from Latin alphabet (a-z)
- Require at least one number
These three are self explanatory and should be active within your password policy at the very least, to stop users from creating easy-to-guess and therefore weak passwords.
- Require at least one non-alphanumeric character (! @ # $ % ^ & * ( ) _ + - = [ ] { } | ')
Add this to your password policy to ensure your AWS IAM Users' passwords are even more complex, strengthening the password and making it less susceptible to compromisation.
- Enable password expiration
Enable this setting will give you the option to set a mandatory rotation period. This means if you choose 60 - every 60 days each IAM User will be forced to rotate their passwords. Passwords unchanged over time post a great security risk.
- Password expiration requires administrator reset
If a user has not reset their password within the above mentioned rotation period, they will not be able to reset their password without the assistance of an Administrator - this is designated by yourself and any users with Admin permissions assigned within AWS IAM. This is potentially quite disruptive as it will lock a user out of resetting their own password - but it creates a process where every expired reset raises a notification.
- Allow users to change their own password
Grants each AWS IAM User the ability to change their own password - useful if you have set a rotation period to each IAM User.
- Prevent password reuse
This setting will block Users from re-using passwords they have previously used for this particular AWS IAM User. You can also configure AWS to remember x number of passwords, so they there is a small history for each IAM User in which AWS performs this check.
AWS Config Rule: IAM Password Policy
Within the StackZone Config Rules, there is one which focuses on the above IAM Password Policy. You can read the current article on this Config Rule, which includes how to resolve this config rule manually, and automatically via StackZone.
This would be useful if you want to monitor this Policy across a lot of AWS Accounts under your Organization.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


