How To Enable AWS SSO with StackZone
Including StackZone SSO Permission Sets
Ryan Ware
Last Update 2 years ago
AWS Single Sign On (SSO)
AWS Single Sign-On (SSO) is an incredibly useful tool if your Organization has more than one AWS account, on top of being incredibly useful for managing access into each account, it removes a lot of the complexity associated with having individual IAM accounts per account.
AWS Single Sign-On is a cloud-based single sign-on (SSO) service that makes it easy to centrally manage SSO access to all of your AWS accounts and cloud applications. Specifically, it helps you manage SSO access and user permissions across all your AWS accounts in AWS Organizations. AWS SSO also helps you manage access and permissions to commonly used third-party software as a service (SaaS) applications, AWS SSO-integrated applications as well as custom applications that support Security Assertion Markup Language (SAML) 2.0. AWS SSO includes a user portal where your end-users can find and access all their assigned AWS accounts, cloud applications, and custom applications in one place.
One of the benefits of using AWS SSO to manage authentication and console / CLI access into your AWS accounts is that you can build permission sets per account, and then assign, remove or re-assign users to as many or as few of these permission sets as you desire.
Do you need Team A to access 5 different accounts but have different permission levels in each? But Team B share the last 2 permission levels only? AWS SSO Permission Sets allow you to control this, and granularly monitor which role or permission set each user assumes.
Whilst AWS SSO is an alternative to using IAM users and roles, it does not nullify any resources created thus far within IAM. You can use these in conjunction if you so desire.
AWS SSO Permission Sets also carry a defined lifecycle, which means you can let a user assume a level of permissions available to them, for a set amount of time. Short-Lived credentials are a useful tool in minimising risk especially when it comes to permissions which have a high level of access.
StackZone AWS SSO
When using StackZone to set up your AWS SSO Instance, you will first need to enable AWS SSO in your Organization's Primary Account. Ensure that when you create your AWS SSO Instance, it is in the desired region, which may or may not be your Primary Region.
Open the AWS SSO Console, and choose Enable AWS SSO
Once this has been enabled, you will need the AWS SSO ARN in order to complete the StackZone AWS SSO resource setup. This can be found from the AWS SSO Console, under Settings from the left hand side menu. The very top listed bit of information is your AWS SSO Instance ARN - and looks similar to this; arn:aws:sso:::instance/ssoins-7548adc379b88735
You will also need to add your AWS SSO Region in here
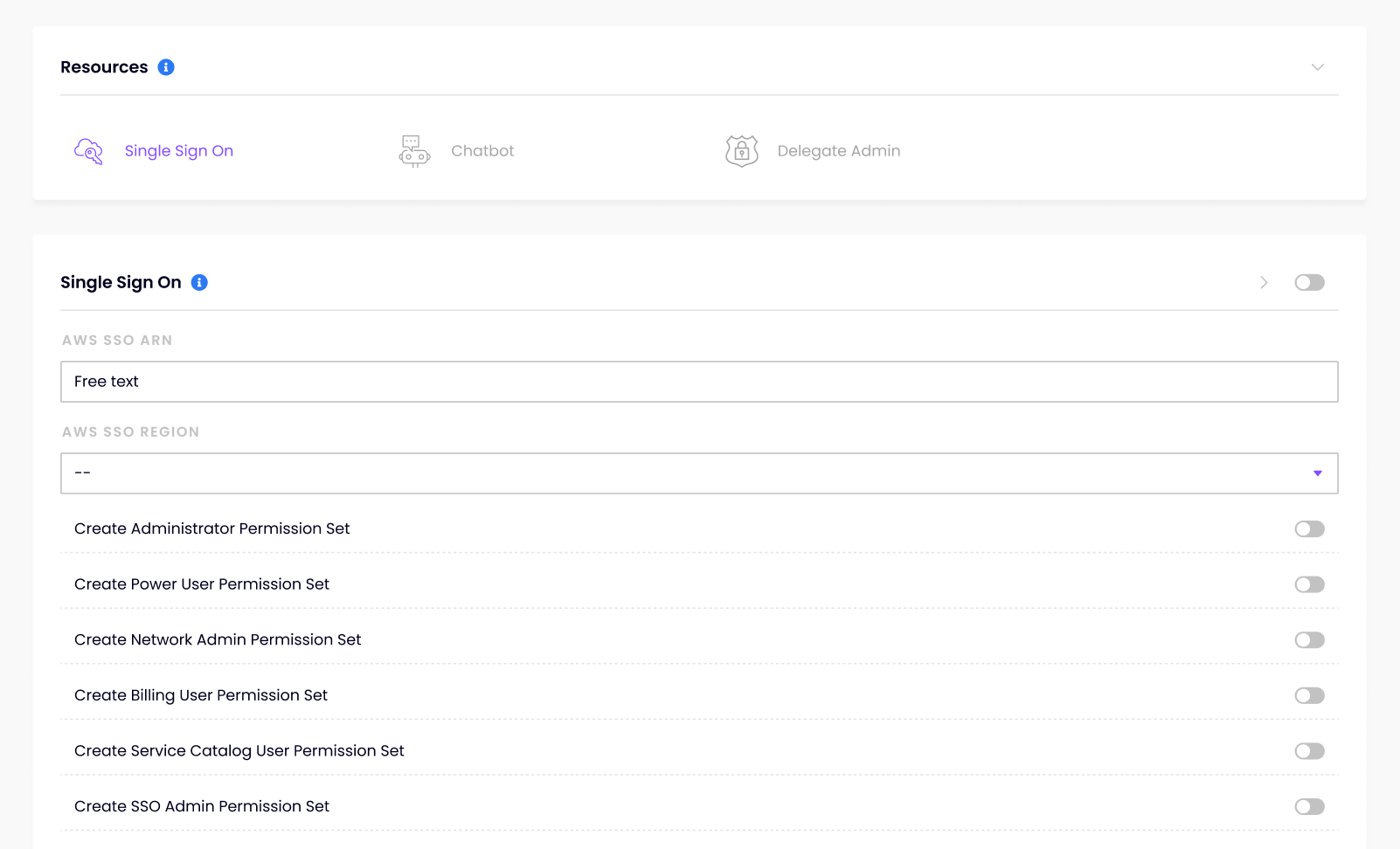
SSO Permission Sets
Administrator Permission Set:
The Administrator Permission Set is a highly permissive role for an SSO User to assume, which provides full access to all actions and services within your AWS Account. The Permission Set is not to be used lightly, as anyone entrusted with this level of permissions has the ability to create, edit, move, delete virtually all AWS resources within the account this Permission Set has been assigned to for the SSO User.
Power User Permission Set:
The Power User Permission Set is very similar to the above mentioned Administrator Permission Set, however the ability to manage Users and Groups within your AWS account has been removed.
For example, an SSO User with this Permission Set will be able to use the DescribeOrganization API call, but no others from the organizations actions list.
Within IAM, this user will be able to list roles, create and delete service linked roles only, but all other actions within IAM are restricted.
Org Admin Permission Set:
The Organization Administrator Permission Set is useful to delegate to any SSO User who needs to manage the AWS Organization of which you belong to. AWS Accounts can be grouped within an AWS Organization and your AWS SSO Instance may reside within this Organization, under a specific AWS Account.
This Permission set will allow an SSO User to manage the AWS Organization from an administrative level, such as creating AWS accounts, creating additional Organizational Units, creating and attaching policies and more.
For more on the list of available actions, see this AWS Organizations API Operations list here
Network Admin Permission Set:
The Network Administrator Permission Set is similar to the Power User Permission Set, but is more focused on AWS Networking resources. This Permission Set is useful if you wish to assign access permissions to an SSO User in order to set up and configure services which revolve around Networking in AWS.
These services are mostly confined to the AWS EC2 Service, as VPC elements live within here, however the services list also stretch out to DirectConnect, CloudFront, Elastic Beanstalk and Route 53 for DNS configuration. There are also minimal permissions to SNS, CloudWatch Logs, S3 and IAM to aid with permissions.
Billing User Permission Set:
The Billing User Permission Set grants permissions to an SSO User for billing and cost management. This includes viewing account usage through the Billing and Usage sections of the AWS Portal along with the ability to view and modify AWS Budgets.
This Permission Set also allows you to work with Cost and Usage Reports (CUR) and Cost Explorer which is a handy tool in the AWS Billing world. Another aspect here you're authorized to make use of is the Purchase Orders which gives you the ability to view and modify Purchase Orders in your account.
Service Catalog User Permission Set:
The Service Catalog User Permission Set provides full access to service catalog end user capabilities in your designated AWS Account. When you add or launch products from your Service Catalog, you will have the required permissions to interact with CloudFormation, as this Permission Set specifically allows access over Stacks and StackSets which are prefixed by either "SC-" or "StackSet-SC-", ensuring that your level of access with CloudFormation stays within it's intended scope.
The Permission Set will also allow the SSO User a small amount of permissions with SSM in order for them to view Documents and Automation Executions, along with read access to AWS Config so that they can read information on their account's Configuration Recorder.
SSO Admin Permission Set:
The Single Sign-On (SSO) Permission Set is useful if you have users in charge of managing your AWS SSO Instance, and the users assigned therein.
This Permission Set has full access over sso-directory: and sso: api calls, along with some access with Directory Service and Organizations to help manage your AWS Organization - but the access around AWS Organizations is not as powerful as the Org Admin Permission Set - so you will need to use both if an SSO User is required to manage both aspects.
Data Scientist Permission Set:
The Data Scientist Permission Set is useful if you have users that are working with Machine Learning services.
This is a job-function Permission Set which grants permissions to AWS data analytics services. You can read what specific permissions are given here.
Fleet Manager Permission Set:
The Fleet Manager Permission Set is designed for use with AWS' Systems Manager (SSM) Fleet Manager dashboard. If you are using SSM Fleet Manager to manage your AWS EC2 Instances, this Permission Set is perfect to assign to an SSO User in order to allow them to continue managing your instances. Whether that be starting SSM sessions, send commands through the SSM Agent, or retrieving SSM Documents - providing the access check has passed, however.
Read Only Permissions Set:
The Read Only Permission Set is useful if you need to give access to to an SSO User or Group to a particular AWS Account without the fear of them making changes to the environment in any way.
This is an appropriate SSO Permission Set if you need to let someone into your AWS Environment to view and review current architecture. They will be able to see all of your EC2 Instances and their configuration, but not start and stop any of them for example.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


