StackZone Feature: GuardDuty
Core Accounts Security Feature
Ryan Ware
Last Update hace un año
A Global Centralized Amazon GuardDuty for all your accounts within your StackZone Organization. It gives your SecOps team full visibility of findings. Any new account gets invited to the centralized Amazon GuardDuty Detector.
What is Amazon GuardDuty?
Amazon GuardDuty is a threat detection service that continuously monitors your AWS accounts and workloads for malicious activity and delivers detailed security findings for visibility and remediation.
This service is designed to scan contents inside your container workloads, S3 Buckets, compute instance workloads along with AWS Accounts and Users for potential threats at scale. GuardDuty uses machine learning anomaly detection, malware scanning and integrated threat intelligence to identify possible threats inside your resources.
To learn more about this AWS Feature, head on over to their official documentation linked here.
How to Enable GuardDuty with StackZone
GuardDuty is enabled in your Security Account and can therefore be found in the StackZone console under Core Accounts / Security / GuardDuty
You can enable it like so, take a look at the image below as an example. Below we will outline what each aspect of the feature means so you can monitor only what you want to.
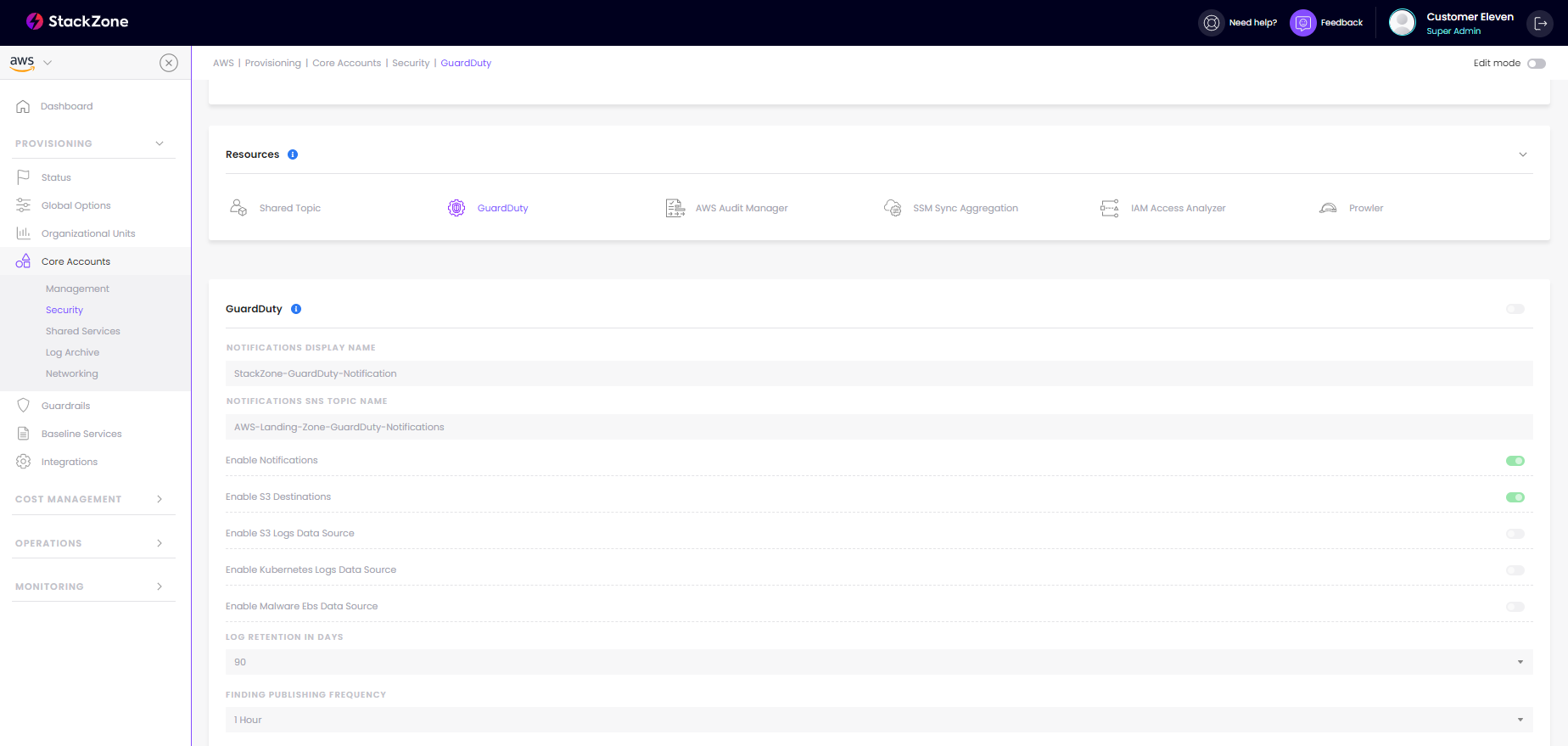
Notifications Display Name:
This is simply the SNS Display name for security administrator(s). It defaults to "StackZone-GuardDuty-Notification"
Notifications SNS Topic Name:
This is the SNS topic name for security notifications. It defaults to "AWS-Landing-Zone-GuardDuty-Notifications"
Enable Notifications:
This will enable GuardDuty Notifications via Events Rule, forwarding onto your SNS Topic
Enable S3 Destinations:
This will enable logging of GuardDuty Findings to your Amazon S3 Bucket located in the Log-Archive Account. We will use the stackzone-logs bucket located in this centralized logging AWS Account within your StackZone OU.
Enable S3 Logs Data Source:
This will enable or disable S3 Data Events as a DataSource to be scanned by GuardDuty. Data Events can be quite costly if you are a heavy S3 user so be cautious with enabling this particular part of GuardDuty
Enable Kubernetes Logs Data Source:
This will enable or disable Kubernetes (EKS) Logs as a DataSource to be scanned by GuardDuty
Enable Malware EBS Data Source:
This will enable or disable EBS Volumes as a DataSource to be scanned by GuardDuty
Enable RDS Login Events Data Source:
This will enable or disable monitoring and generate findings for RDS login events to protect your Amazon Aurora databases
Enable Runtime Monitoring Data Source:
This will enable or disable the ability to monitor runtime activity to detect threats to your Amazon ECS (Including Fargate) and Amazon EC2 workloads. To use Runtime Monitoring, you also need to manage a GuardDuty security agent that will ingest runtime activity for your resource.
Enable EKS Runtime Monitoring Data Source:
This will enable or disable the ability to monitor runtime activity to detect threats to your Amazon EKS workloads. To use Runtime Monitoring, you also need to manage a GuardDuty security agent that will ingest runtime activity for your resource.
Enable Lambda Network Logs Data Source:
This will enable or disable network activity monitoring for Lambda function logs.
Log Retention In Days:
This specifies the amount of CloudWatch Log Group retention in days for notifications forwarding log events in the Lambda log group
Finding Publishing Frequency:
This specifies how frequently updated findings are exported. By default this is 1 Hour, but you can change this to 6 Hours or 15 Minutes depending on your preference
StackZone GuardDuty Notifications
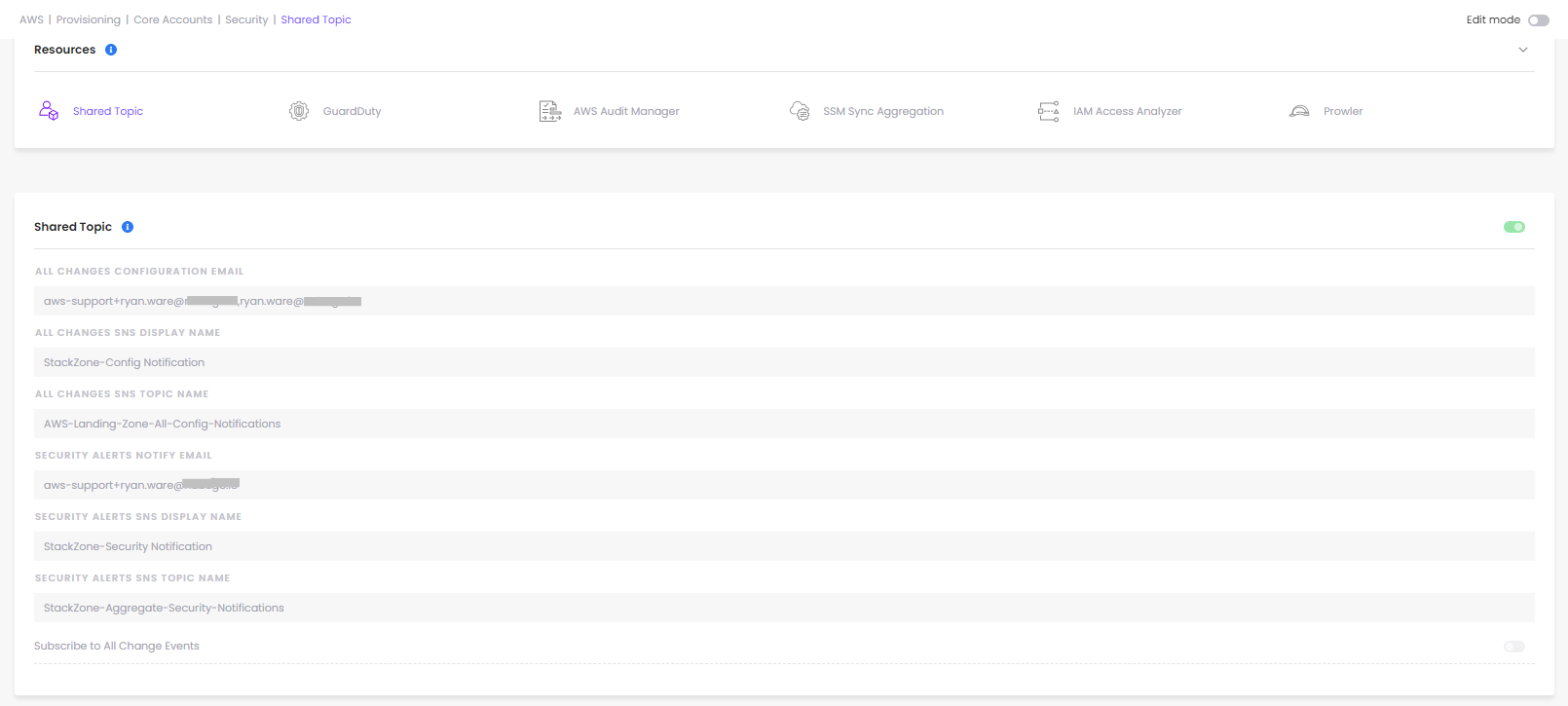
The process for notifications starts with GuardDuty itself, when we publish from GuardDuty to the SNS Notification Topic, which by default is set to "AWS-Landing-Zone-GuardDuty-Notifications"
Subscribed to this SNS Topic is a Lambda Function we deploy which will then forward these events onto the Security Topic, which was constructed in order to aggregate Security Notifications, this SNS Topic will likely be called "StackZone-Aggregate-Security-Notifications" and will be present within the Security Account of your StackZone deployment.
You will need to subscribe to this SNS Topic in order to receive all notifications which are sent to this aggregated Security SNS Topic. This can be configured in the Provisioning / Core Accounts / Security / Shared Topic feature within StackZone Console. You can see below in the example we are subscribing the email address listed within "Security Alerts Notify Email" to the SNS Topic "StackZone-Aggregate-Security-Notifications"
F.A.Q.
Q: How do I enable Protection Plans for Member Accounts?
A: To enable this for your GuardDuty Member Accounts, head to the GuardDuty Master Detector in your Security Account and choose Accounts. From here you can enable or disable Protection Plans for your individual member accounts for enabled Protection Plans which StackZone enabled for you.

Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here.


