StackZone Feature: GuardDuty Remediations
Protect your network and instances with GuardDuty Remediations
Ryan Ware
Last Update 2 years ago
This article will explain how you can use StackZone GuardDuty Remediations to apply protection to your VPC Networks and EC2 instances by reacting to threats by building ACL's which block inbound traffic from bad actors.
We can perform these actions based off what we receive from GuardDuty Findings. There are a large number of GuardDuty Findings available but today we are going to focus on EC2 and Networking Findings which could potentially cause harm and disruption to your instances or services. Just some of these GuardDuty Findings can be seen below:

GuardDuty Remediations
GuardDuty Remediations will protect your VPC networks and EC2 Instances from additional potential attack threats and vectors. When we receive one of a number of GuardDuty Findings which could be an attack on one of your instances, we take action by blacklisting the source IP of the attacker from VPC network by creating ACL's (Access Control Lists) which deny incoming traffic from said source IP.
For example, we set up some triggers by building a "Red Team" attack instance in an AWS VPC with an internal IP of 172.16.0.29 and ran some tests against a target instance, in the same VPC.
GuardDuty successfully identified these attacks and you can see the findings below against our target instance:
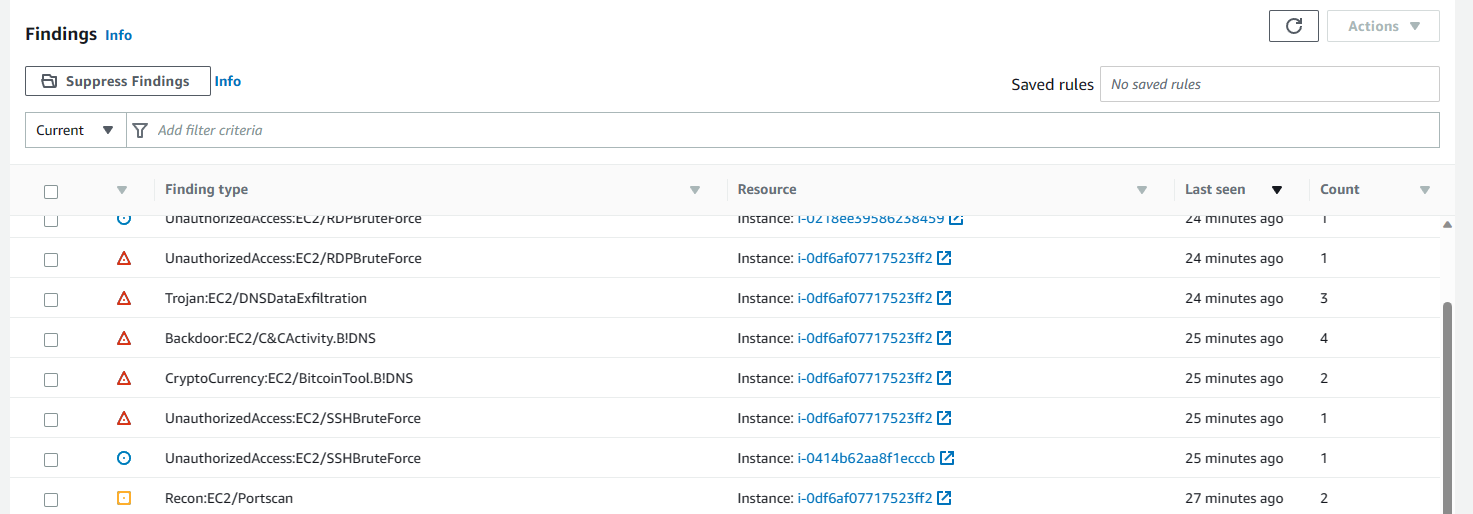
With this knowledge from the GuardDuty Findings, we are able to determine the source IP of these attacks. We apply the remediation through a Lambda Function which adds ACL rules to the VPC in which the target instance resides in.
This from a networking perspective blocks all incoming traffic from the source IP of the attacking instance inbound to the VPC where our target EC2 instance lives. Here you can see evidence of this in action by reviewing the three new rules we created for the VPC ACL's:
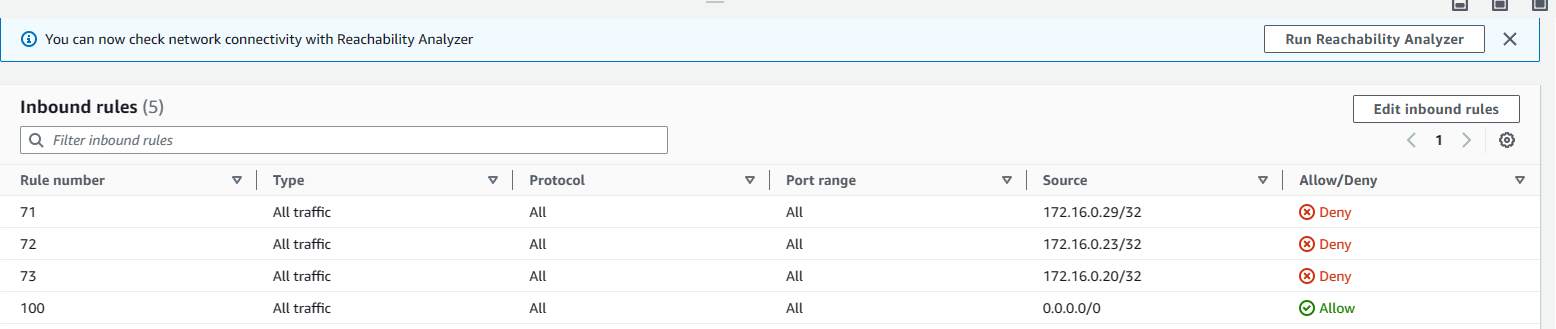
It is worth noting that during our testing we saw our first GuardDuty Finding reported, 8 minutes later the Remediaiton had constructed the first ACL which would block traffic from the bad actor instance. This is potentially faster than if these GuardDuty Findings were being monitored and reviewed in real time.
If you want to learn how StackZone can build GuardDuty Findings Advanced Notifications for your team, see this article.
In order to activate this feature, head on over to Provisioning in your StackZone Console, then onto Core Accounts / Security / GuardDuty and enable GuardDuty Remediations.
F. A. Q.
Q: What is NACL retention in the console?
A: This setting determines how long to retain IP addresses in the blacklist (in minutes). Default is 12 hours, minimum is 5 minutes and maximum one week (10080 minutes)
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


