StackZone Feature: SSO Tags
Introduced in v4.19.0 of StackZone
Ryan Ware
Last Update 3 ปีที่แล้ว
AWS Single Sign-On
This Feature is designed to help you tag at scale your AWS Accounts from the AWS Organizations menu, which assigns Amazon Single Sign-On (SSO) Permission Sets to AWS SSO Groups per account.
Instead of navigating through the AWS SSO Menu for each group and permission set for every account, you can slimline this process by tagging your accounts. StackZone will then complete the necessary steps to assign an SSO Group to that AWS Account and give them the required SSO Permission Set, declared in the Tag value.
AWS Single Sign-On (AWS SSO) is where you create, or connect, your workforce identities in AWS once and manage access centrally across your AWS organization. You can choose to manage access just to your AWS accounts or cloud applications. You can create user identities directly in AWS SSO, or you can bring them from your Microsoft Active Directory or a standards-based identity provider, such as Okta Universal Directory or Azure AD.
For more information on AWS SSO, please see their official documentation linked here.
StackZone SSO Tags
How do we get started with this? To begin we will need to head on over to the AWS Organizations dashboard which will be located in your StackZone Primary Account. AWS Organizations is Global, so don't worry about what region you are in, within the AWS Console.
Once you have your Organizational Tree in front of you, select which AWS Account you want to tag, and click into this. You will see Tags as the first of three tabs below the AWS Account Information. We want to add a tag which is very similar to this format. Take a look at how the / is used as we can assign an SSO Permission Set to multiple SSO Groups!
Key: sso_1
Value: ps-0e7b96af08e1eb3d@Billing/Devs
What does this mean? The first part of the Value is the SSO Permission Set. We'll show you how you can find the correct one further below. The second part of the Tag Value is after the @ and list the SSO Groups we're adding. They are seperated by /
Find your SSO Permission Set ID
To find out which AWS SSO Permission Set ID you will need for the above Tag Value, head on over to your AWS SSO Instance which will be created in your StackZone Primary Account and hosted within the Primary Region, whichever that is for your deployment.
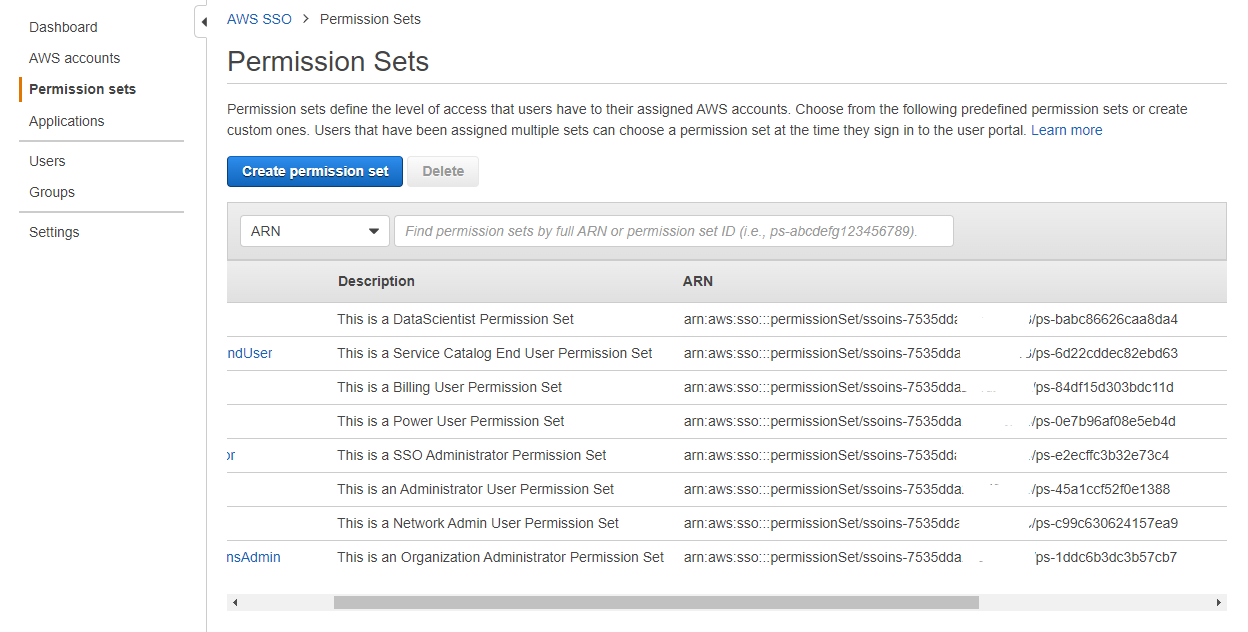
Under the left hand side menu, choose Permission Sets and you will see an overview of all current Permission Sets. If you look at the ARN of each Permission Set, we want the last part of the full arn to use in the above tag value
ps-123abcfa1234abcfa4
Choose Your AWS SSO Groups
The second part of the Tag Value after the @ symbol pertains to the AWS SSO Groups. You can see these from the AWS SSO Dashboard under the Groups section. We are using the Group Name here.
For example, by using the following Group Value "@Billing" - this will apply the Billing Group to the tagged AWS Account using the defined AWS Permission Set.
If we also use the Group Value "@Billing/Devs" this will apply both Billing and Devs Groups to the tagged AWS Account.
Check the Results
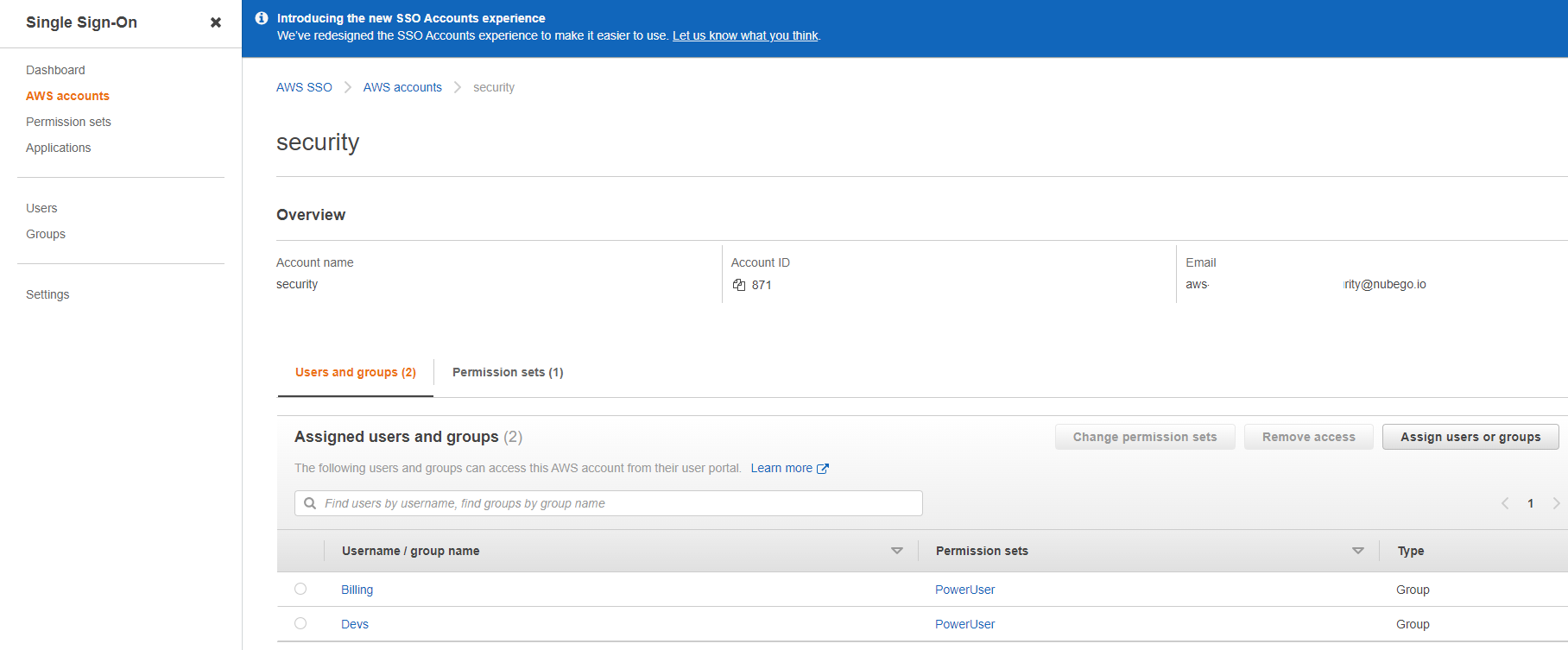
Let's take a look at the result! By reviewing the AWS Account "Security" which was tagged originally, we can see that two SSO Groups have been added to this AWS Account and have been permitted to use the AWS SSO Permission Set "PowerUser" which pertains to the Permission Set ID listed above.
StackZone will run periodically to apply these SSO changes to your AWS Accounts. The rate of this can be adjusted to your liking in your StackZone configuration for this particular feature.
Want to know more about StackZone and how to make your cloud management simple and secure?
Check our how it works section with easy to follow videos or just create your own StackZone Account here


